Phishing has been and continues to be one of the most common methods (TTPs) cyber attackers use because it is so effective. Phishing is a simple attack vector that enables cyber attackers to easily scale their attacks, customize for their intended targets, and bypass many security controls. Reports like the Verizon DBIR or the Microsoft Digital Defense continue to identify phishing as a top risk. While technologies like email filtering (example Proofpoint) and EDR (example Crowdstrike) make it much more difficult to succeed, cyber attackers have continued to adapt.
Several phishing trends we are seeing
Over the past several years phishing has continued to evolve. While many of the emotional lures used to get people to click and fall victim remain the same (covered in more detail below), we have seen changes in both cyber attacker modalities and goals. Here are some of the most common phishing trends we are seeing.
Modalities
Traditionally phishing was done through email. However, we have seen a dramatic shift where messaging technologies are also being used, to include Apple iMessage, WhatsApp, and standard SMS functionality. Texting has become increasing popular, as many phones lack any type of filtering capability, which means the scams and attacks are far more likely to get through. Also, since text messages tend to be much shorter with little context, it’s much harder to confirm what is legitimate versus what is an attack. As such, when training your workforce emphasize that phishing attacks happen not just over email, but via any messaging technology.
Goals
The goal with phishing attacks traditionally was for people to install malware on their computer and infect their systems for the cyber attacker. However, malware infections are becoming easier and easier for security teams to detect, so that behavior has radically changed. In today’s world we are seeing three different goals of phishing attacks:
- Passwords: One of the top goals we’re seeing is to get people to click on a link that takes them to a website that harvests their passwords. Once an individual’s credentials are stolen, cyber attackers can cause a great deal of damage while operating undetected.
- Phone: An increasing number of phishing attacks do not have a link but phone number as their point of attack. The cyber attacker’s goal is to get the victim to call a phone number. Once the victim is on the phone, cyber attackers will use stories and emotion to pressure people into taking actions, such as giving up their passwords, purchasing gift cards, or transferring money from their bank accounts to accounts controlled by the attacker. Attackers have learned that while these attacks can take a great deal more work, seeing as they are not automated, they can be far more successful and profitable, as they can fool people out of their checking, savings, or retirement accounts, stealing their entire life savings.
- Scams: Many phishing emails have no link or attachment. Instead, the messages are often very short and impersonate someone that the victim knows or trusts, such as their boss, a co-worker or a company with which they work or shop. BEC attacks are a common example (covered in more detail below)
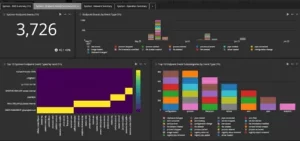
One way you can determine what type of phishing attacks your organization is seeing is to check with your Cyber Threat Intelligence team, your Email Support team, or anyone responsible for your email filtering or perimeter defenses. If you have some type of anti-phishing solutions (such as Proofpoint) your security team can log and categorize the type of phishing attacks your organization is seeing. Below is an example of a real report generated by Proofpoint for a real company. In this chart we see the following:
_-_Blog_Asset_1_-_2.9.23_(1).jpg)
- 69% of all phishing emails attempt to take you to a website to gather information (via clicking on a URL or opening an email attachment). This is primarily for password harvesting but sites may also include “surveys.”
- 14% are imposter messages. These would include scams such as BEC attacks, gift card scams or billing / invoice scams.
- 8% are Telephone Oriented Attack Delivery (TOAD) attacks. This is a new category that Proofpoint added in 2023 due to the increase of these type of phishing attacks. The goal is to get the victim to call a phone number.
- Only 9% of all phishing emails are attempting to infect the victim with malware (via clicking on a URL or opening an email attachment).
Common phishing indicators
We do not recommend that you try to teach people about every different type of phishing attack and every lure possible. Not only is this most likely to be overwhelming to your workforce, but cyber attackers are constantly changing their lures and techniques. Instead, focus on the most commonly shared indicators and clues of an attack. This way your workforce will be trained and enabled regardless of the method or lures that cyber attackers use.
In addition, emphasize that phishing attacks are no longer just email but use different messaging technologies. That is why these indicators are so effective: They are common in almost every phishing attack, regardless of whether it’s via email or messaging. The most common indicators include:
- Urgency: Any email or message that creates a tremendous sense of urgency, trying to rush the victim into making a mistake. An example is a message from the government stating your taxes are overdue and if you don’t pay right away you will end up in jail.
- Pressure: Any email or message that pressures an employee to ignore or bypass company policies and procedures. BEC attacks (covered below) are an example.
- Curiosity: Any email or message that generates a tremendous amount of curiosity or is too good to be true, such as an undelivered UPS package or you are receiving an Amazon refund.
- Tone: An email or message that appears to be coming from a coworker, but the wording does not sound like them, or the overall tone or signature is wrong.
- Generic: An email coming from a trusted organization but uses a generic salutation such as “Dear Customer.” If FedEx or Apple has a package for you, they should know your name.
- Personal Email Address: Any email that appears to come from a legitimate organization, vendor or co-worker, but is using a personal email address like @gmail.com.
Phishing indicators we no longer recommend
These are typical indicators that have been recommended in the past but we no longer recommend them:
- Misspellings: Avoid using misspellings or poor grammar as an indicator of phishing. In today’s world you are more likely to receive a legitimate email with bad spelling than a crafted phishing attack.
- Hovering: One method commonly taught is to hover over the link to determine if its legitimate. We no longer recommend this method except for highly technical audiences. One problem with this method is that you have to teach people how to decode a URL, which can be a confusing, time consuming, and technical skill. In addition, many of today’s links are hard to decode as they are re-written by phishing security solutions such as Proofpoint. Finally, it can be difficult to hover over links with mobile devices, which is one of the most common ways people read email.
Source: https://www.sans.org/blog/phishing-its-no-longer-about-malware-or-even-email/
About DT Asia
DT Asia began in 2007 with a clear mission to build the market entry for various pioneering IT security solutions from the US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around the Asia Pacific to better understand the markets and deliver localised solutions.