Check out these graphic recordings created in real-time throughout the event for SANS Security Awareness: Managing Human Risk Summit 2024
How to optimize NetFlow for Splunk
Explore the world of network optimization and advanced analytics with our comprehensive guide on optimizing NetFlow for Splunk. In this blog, we’ll refer to all flow protocols, such as sFlow, JFlow, IPFIX, and cloud flow logs, collectively as ‘NetFlow.’ Discover how to unlock the full potential of these technologies for unparalleled network visibility and deep analysis. From enabling NetFlow on your devices to integrating it seamlessly with Splunk, we’ll walk you through each step. Plus, we’ll provide troubleshooting tips and best practices to ensure top performance and extract the maximum value from your network traffic data. Get ready to elevate your network monitoring and analytics!
Understanding the NIS 2 Directive and Its Relevance for EU companies
The NIS 2 Directive marks a significant advancement in cybersecurity across the European Union, particularly for sectors vital to society and the economy. Set to take effect by October 17, 2024, this directive introduces comprehensive security measures for companies in key industries, mandating that they bolster their information systems and safeguard data against cyber threats. Unlike the GDPR, which focuses solely on personal data, NIS 2 has wider implications, impacting all companies that meet specific thresholds or operate within sectors critical to national infrastructure.
PostgreSQL — Your next database platform?
As a database administrator, you’re likely recognized for your practical approach to technology within your organization. While it’s essential to continually sharpen your skills, what really matters is having a database solution ready when a new application question arises. In recent years, many developers have been asking for PostgreSQL (commonly known as “Postgres”) due to its broad functionality. It’s no wonder Postgres was ranked the number one “most-wanted” database in Stack Overflow’s 2021 Developer Survey, surpassing even Redis and MongoDB.
SecureUSB® Drives Can Help Prevent Data Breaches
In today’s digital landscape, data security is more crucial—and more at risk—than ever. Our most sensitive information is shared and stored online daily, making it increasingly vulnerable to data breaches.
How to tap into the full power of open banking APIs
Over the past decade, many banks have launched developer portals to share their open APIs, allowing developers to sign up and use these APIs to drive their business initiatives. But is this truly open banking in action?
Enhancing Industrial Control System Security in Manufacturing with PrivX
As manufacturing increasingly relies on automation and interconnected systems, the security of Industrial Control Systems (ICS) is becoming more critical than ever. A breach in ICS can result in significant downtime, safety hazards, and substantial financial losses. Given the evolving sophistication of cybercriminals, advanced security solutions are essential to protect critical infrastructure. PrivX offers powerful tools to enhance ICS security, ensuring safe and compliant operations in the manufacturing sector.
Where does data destruction fit in the IIoT
Fifteen years ago, the concept of a “computer” was much simpler—limited to desktops, basic mobile phones, and other standard devices. Today, the Internet of Things (IoT) has drastically expanded that definition, embedding processing power and data storage in everything from smartphones to smart vehicles. However, this evolution has also introduced new security challenges. Unlike traditional IT devices, Industrial IoT (IIoT) hardware is designed to endure harsh environments, making data destruction more critical. As these devices store valuable data, robust data destruction methods must be employed to prevent unauthorized access.
What is Your Definition of Insider Threat?
How you define insider threat is critical, because how the problem is defined will drive how you define and implement the solution.
Key Features of NetFlow Optimizer
NetFlow Optimizer offers powerful capabilities tailored for network administrators and security professionals. It empowers organizations to fully leverage NetFlow data, enhancing network security and IT operations. Whether focusing on proactive network traffic monitoring or ensuring top-notch security, these key features provide essential tools to meet your needs effectively.
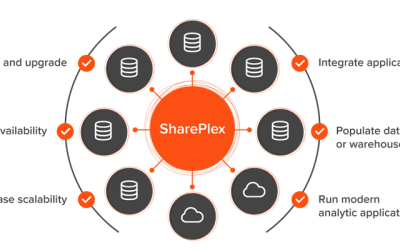
What is dynamic data movement?
Dynamic data movement involves replicating data from traditional RDBMS systems like Oracle to other databases such as MySQL, Azure SQL Database, Kafka, and PostgreSQL.
Let’s Discuss Data Sanitization: Misconceptions, Misinformation, Reality.
In the digital age, concerns about data management and privacy are rapidly growing as the volume of data increases exponentially. With regulatory compliance and data privacy issues becoming more prominent, it is the responsibility of the IT industry to ensure data security and prevent leaks by implementing proper data sanitization procedures and tools.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065