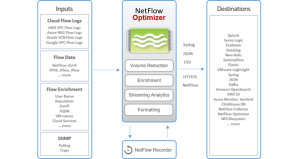
Tectia SSH Client/Server by SSH Communication Security is not affected by XZ/liblzma
How does the backdoor work?
How was the liblzma backdoor injected into the library?
How dangerous is the liblzma?
Ubuntu 24.04LTS was just a month away from being released with this backdoor, and other distributions were in a similar situation. Perhaps the most apt description is this: if left undiscovered, Linux servers would have been operating with a dormant threat waiting to be remotely activated. CVE-2024-3094 acts like a digital sleeper agent, awaiting a trigger to potentially unleash one of the most devastating cyberterrorism acts ever seen.
How was liblzma discovered?
Fortunately, this backdoor was detected early, ensuring the safety of most of the Linux user community. Much of the credit belongs to Andres Freund from Microsoft, who diligently investigated the slowdown in the PostgreSQL test lab and uncovered the liblzma backdoor.
Thank you, Andres, for your dedicated efforts! Your work deserves global acknowledgment for averting what could have been a worldwide disaster.
Open source is free but comes with a cost
Regarding the risks associated with voluntarily maintained projects becoming integral to larger ecosystems: Users of open-source software (OSS) projects benefit from the original author’s work, often without adequate compensation or support. This imbalance can lead to a significant support burden on maintainers, eventually wearing them down.
Bad actors volunteer to assist maintainers, possibly leveraging social pressure as a tactic. In return, they gain influence over the project, riding on the reputation of the original author and the established user base. The consequences are evident in hindsight.
Source: https://www.ssh.com/blog/a-recap-of-the-openssh-and-xz-liblzma-incident
About DT Asia
DT Asia began in 2007 with a clear mission to build the market entry for various pioneering IT security solutions from the US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around the Asia Pacific to better understand the markets and deliver localised solutions.