In today’s rapidly evolving cyber threat landscape, organizations face constant challenges in outpacing increasingly sophisticated attacks. Traditional security solutions often fall short, leaving critical vulnerabilities exposed. Enter NetFlow: a transformative tool that redefines how organizations approach threat detection and response.
Your data is at risk from quantum computers right now. Here’s why.
Quantum computers exist as we speak. While their full potential will still be years in the making, your business needs to start upping the ante on the encryption game without delay.
Compliance with Data Protection Regulations
Data security has transformed from a behind-the-scenes IT function to a critical business priority. This evolution stems from the increasing prevalence of data breaches that expose sensitive consumer information. In response, governments worldwide have established stringent regulations requiring organizations to safeguard Personally Identifiable Information (PII) through encryption and other protective measures.
The Benefits of One Identity Active Roles – Based on PeerSpot Real User Feedback
One Identity Active Roles is a robust identity and access management (IAM) solution designed to streamline and secure Active Directory (AD) environments. By consolidating AD domains and Entra ID tenants into a unified console, Active Roles ensures consistent enforcement of security policies through automation, granular delegation, and permissions management. This not only synchronizes identity data across the network but also reduces instances of incorrect access privileges, ultimately strengthening organizational security and efficiency.
API as a Product: an enterprise strategy for business growth while avoiding catastrophe
Fail Fast, Move Forward: Embracing the API-as-a-Product Mindset
SSH’s PrivX OT and Honeywell Provide a Comprehensive OT Security Solution
Operational Technology (OT) security is a multifaceted challenge, requiring organizations to address diverse risks and vulnerabilities. Frameworks like the NIST Cybersecurity Framework 2.0 (CSF 2.0) help structure these efforts. Although not OT-specific, CSF 2.0 provides valuable guidance for improving cybersecurity across industries. In Europe, frameworks like NIS2 extend these protections, emphasizing the security of critical infrastructure.
Understanding the NIS 2 Directive and Its Relevance for EU companies
The NIS 2 Directive represents a pivotal advancement in enhancing cybersecurity within the European Union, targeting sectors essential to societal and economic operations. Effective October 17, 2024, the directive mandates stringent security measures for companies, compelling them to secure their information systems and shield data against cyber threats.
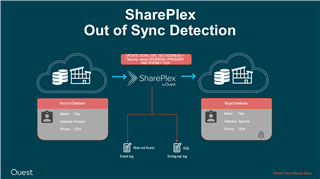
SharePlex Out-of-Sync in Depth
SharePlex users often inquire about how the tool detects, processes, and resolves discrepancies between rows in source and target databases. SharePlex is specifically designed to maintain synchronization in replication streams, addressing cases where the data in source and target databases diverges. In this context, two important terms are “out-of-sync”, which applies to any replication setup, and “conflict”, relevant to bi-directional or peer-to-peer replication.
Introducing GRAYLOG v6.1: New Features Designed to Cut Complexity and Boost Efficiency
It’s no coincidence that Graylog 6.1 is making its debut right before Halloween. This release is a true powerhouse, designed to address some of the most enduring and complex challenges in Security Information and Event Management (SIEM). With a suite of innovative features, Graylog 6.1 is set to redefine how organizations approach security operations.
How Encrypted Drives Prevent Data Loss From Ransomware
As ransomware attacks surge in sophistication and frequency, businesses and organizations of all sizes face heightened risks. These attacks disrupt operations, lead to significant financial losses, and can irreparably damage reputations. Over the past decade, ransomware has grown from isolated incidents to a pervasive global threat, making robust cybersecurity practices essential.
Leveraging NetFlow for Network Security and Threat Detection
In today’s fast-paced cybersecurity landscape, combating sophisticated threats requires innovative tools that provide deep insights. One such powerful tool is NetFlow—a technology that unlocks valuable network traffic data to help organizations safeguard their networks and detect threats. This blog explores the capabilities of NetFlow and its critical role in enhancing network security, revealing hidden risks that could otherwise go undetected. Discover how this remarkable technology can help your organization stay resilient in an evolving threat environment.
NIST Guidelines: Why it’s time to rethink passwords
The landscape of password management is evolving rapidly. Recent guidance from the National Institute of Standards and Technology (NIST) is challenging outdated norms, such as frequent password changes and complex requirements that were once seen as essential to security.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065