News & Events
Security Awareness Training ROI: Part 1 Of 3
Today, data breaches and cyber-attacks are becoming so frequent that they aren’t a matter of “if” but “when,” making cybersecurity employee training a must.
SSH in the World of Post-Quantum Cryptography (PQC)
Nowadays, advances in quantum computing are moving at a neck-breaking pace. Giants in the field have been faithfully executing roadmaps and delivering on milestones laid out several years ago. And while it is hard to predict when the advances will reach their breaking point, the threat to classical, public key cryptography is getting closer.
Yubico Channel Awards 2022
Quote from Yubico:
‘‘Congratulations on the award! Thank you for your partnership over the last several years, we are looking forward to many more joint successes!”
“Congratulations Team DTA! It is our pleasure working and growing with your Team.”
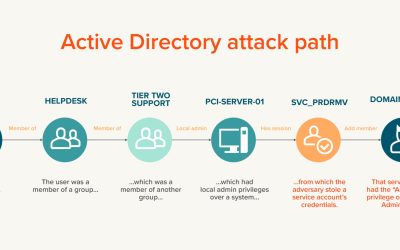
Understanding attack paths targeting Active Directory
Attack paths are at the forefront of cybersecurity discussions today. But exactly what is an attack path? Why is Active Directory (AD) particularly vulnerable? And what can you do to protect your organization? This blog post covers all these questions and more.
Syslog-ng 101, part 5: Sources
This is the fifth part of my syslog-ng tutorial. Last time we had an overview of the syslog-ng configuration and had our first steps working with syslog-ng. Today we learn about syslog-ng source definitions and how to check the syslog-ng version and its enabled features.
Building strong partnerships in Bangkok together with SSH
Quote from SSH:
”Active collaboration is the key. And we are always excited to meet with our partners and plan what the future holds for us together.”
The journey continues – working together towards strong partnerships in Jakarta!
The journey continues – working together towards strong partnerships in Jakarta!
SSH launches new version of Tectia to provide Quantum-Safe communications for US federal government
Helsinki, Finland – March 16, 2023 – The US federal government has shown significant interest in Quantum-Safe communications during 2022, most evidently through Quantum Cybersecurity Preparedness Act, which mandates all electronic communications to be Quantum-Safe after a transition period. The federal government acts as a transformation leader that is followed by other actors in the public sector and even private enterprises.
Let’s Discuss Data Sanitization: Misconceptions, Misinformation, Reality.
In the digital age, concerns about data management and privacy are ever-increasing as the volume of data is increasing exponentially. As regulatory compliance and concerns about data privacy grow, it is the job of the IT industry to ensure data security, preventing leakage, through proper implementation of data sanitization procedures and tools.
YubiHSM 2, the world’s smallest hardware security module, enhanced with new features to support security for the Public Sector
Compliance mandates require many of our customers in regulated industries or in high-risk environments to prove adequate levels of protection for their data, no matter where it lives or travels. This is why we’ve continued to enhance the capabilities of both the YubiHSM 2 and YubiHSM 2 FIPS, the world’s smallest FIPS-validated and non-FIPS hardware security modules (HSMs). Today, we’re also excited to share that the YubiHSM 2 FIPS now meets FIPS 140-2, Level 3. Jump ahead to the “what’s new” section below to learn about the key new features in our YubiHSM 2 products.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065