
When discussing human security, “Insider Threat” is a term that comes up frequently. Many organizations have insider threat programs, but the definition of an insider threat varies significantly from one organization to another. How you define this term is crucial because it directly influences how you approach and implement solutions. While I won’t define insider threat for your organization, I hope to outline different categories that can shape your understanding and explain how these categories impact the solutions you put in place.
What is an Insider Threat?
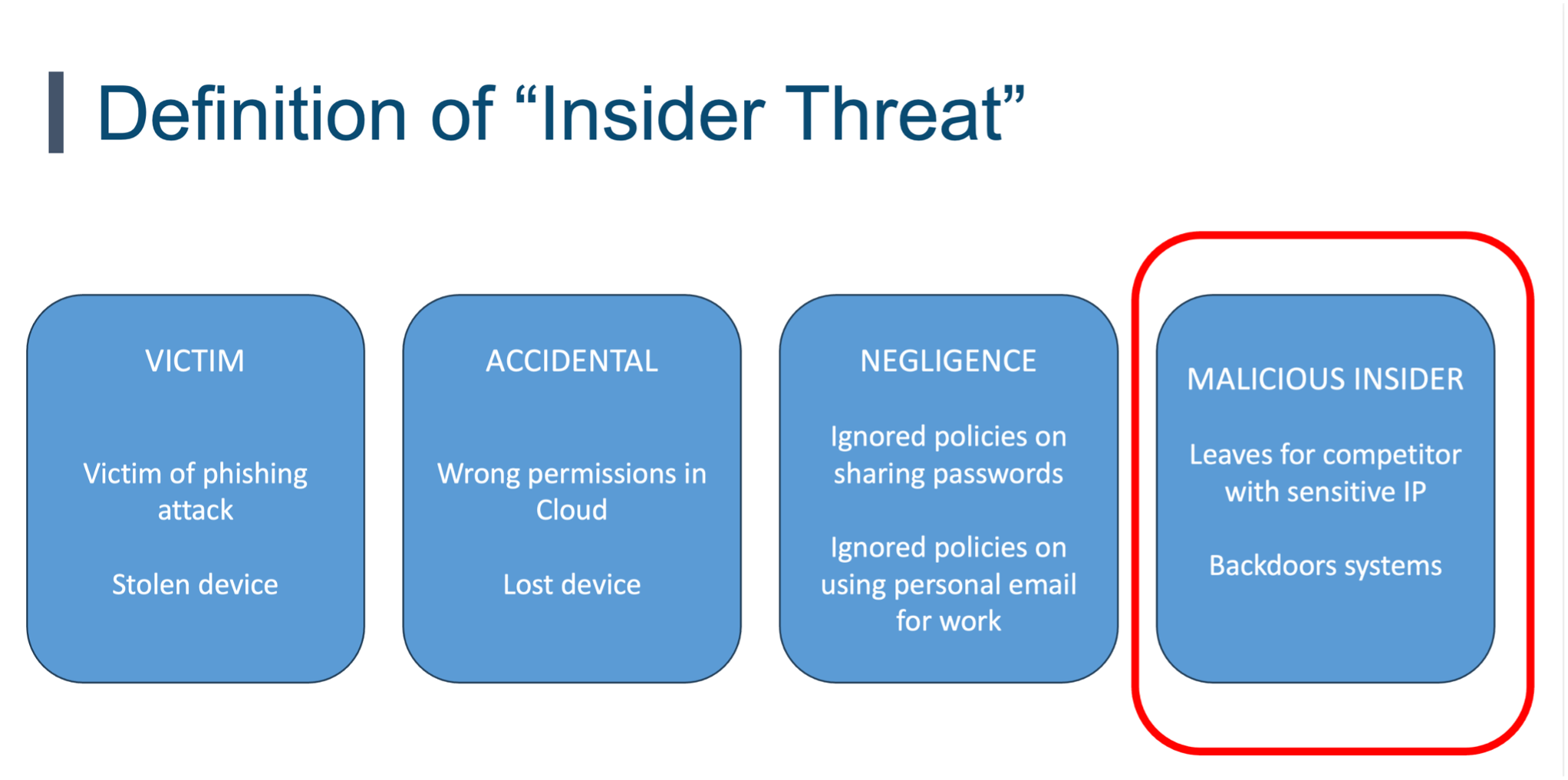
In my experience, insider threats typically fall into four categories. The common thread among them is that they all involve a trusted individual—be it an employee, contractor, intern, or volunteer. Whether you include third-party vendors in this definition is up to you, though they are often managed separately under Third-Party Risk Management (TPRM). The four categories are:
1. Malicious Insider
A malicious insider is a trusted individual who intentionally causes harm. Their motivations can vary—financial gain, revenge, ego, and more. These individuals exploit their trusted access to inflict damage. A typical example is an employee who leaves the company and takes sensitive information, like customer data or trade secrets, with them. Although such incidents are rare, they have a high impact when they do occur. Interestingly, regardless of how organizations define insider threats, this category is often the primary focus of insider threat programs.
2. Negligence
In cases of negligence, harm is not caused intentionally but results from failing to follow security policies and procedures. For example, someone might ignore or bypass security rules to complete their work, such as taking sensitive files home on a personal laptop or forwarding them to a personal email account. While they know they are violating policy, they may feel it’s necessary to do their job. This can indicate that security policies are too complex, confusing, or obstructive to daily tasks.
3. Mistakes
Human error is a significant driver of security breaches. Mistakes happen when people, in the course of their work, inadvertently cause incidents due to carelessness, lack of awareness, or inadequate training. A common example is what Verizon’s Data Breach Investigations Report (DBIR) calls “misdirection,” where an email is accidentally sent to the wrong person due to auto-complete features. For instance, you might intend to email Sarah from finance, but end up sending sensitive documents to your daughter’s basketball coach, who is also named Sarah. Though it might seem trivial, human errors like this account for 25% of breaches globally. This often suggests that technology or policies are too complicated, making such mistakes easier to make.
4. Victim
In this category, the individual becomes a victim of an attack, such as falling for a phishing email or a vishing phone scam.
Define the Solution
The next step is to determine which of these categories fit your definition of an insider threat. This decision is yours to make. However—and this is a crucial point—different categories require different management approaches.
For malicious insiders, you manage the risk similarly to a counter-intelligence program. Start with thorough background checks to hire individuals likely to be trustworthy. Then, implement processes and controls to minimize the damage a trusted individual can inflict. Finally, actively search for signs of malicious behavior—this is challenging because these individuals are trusted, and their motivations or actions often differ from past incidents, making common indicators hard to identify.
For the other three categories—negligence, mistakes, and victimization—your approach should be the opposite. These individuals are good, trustworthy people who want to do the right thing. Your job is to empower them by simplifying security. This is where Security Awareness and Training programs play a vital role. By equipping people with the knowledge, skills, and tools they need, you enable them to use your organization’s technology safely and securely.
The strategy for handling malicious insiders should not only differ but might also need to be led by a separate team, as it requires a unique mindset and skill set. You are essentially hunting for harmful behavior. In contrast, when dealing with negligence, mistakes, and victimization, you are supporting and guiding good behavior.
Ultimately, how you define insider threat is up to you. My only request is that if you use the term “insider threat” or have an insider threat program, clearly define what it means for your organization and adjust your security measures accordingly.
About DT Asia
DT Asia began in 2007 with a clear mission to build the market entry for various pioneering IT security solutions from the US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around the Asia Pacific to better understand the markets and deliver localised solutions.
How we help
If you need to know more about Insider Threat, you’re in the right place, we’re here to help! DTA is SANS Institute’s distributor, especially in Singapore and Asia, our technicians have deep experience on the product and relevant technologies you can always trust, we provide this product’s turnkey solutions, including consultation, deployment, and maintenance service.
Click here and here and here to know more: https://dtasiagroup.com/sans/










