This post is also available in:
 Vietnamese
Vietnamese
Technology has made remote working much more feasible and economical compared to on-site working. Although it is not popular until a decade ago, remote working has now become the new norm of how employees work, especially during the pandemic. In fact, a survey on more than a thousand employees by Airtasker revealed that remote workers are actually more productive than their office-based counterparts.
There was a time when remote working is not even a possibility because of insufficient technology. Now, technology allows us to have more flexibility to work. However, it doesn’t come without a caveat. Along with the increasing numbers of people who work remotely, the digital risk is also rising. Cybercrime is thriving during the pandemic, using time-tested tactics like phishing, social engineering and other hacker methods. Almost 85% of successful data breach is caused by human error rather than computer or system flaws. 61% of all data breaches are the result of schemes that swipe login credentials when accessing the company information system.
Organizations have been trying to mitigate this risk by using Multi Factor Authentications(MFA) and 2FA (2 Factor Authentications), leveraging mobile authentication methods using SMS-based OTP or authenticator apps because of its ease and speed to implement. And yet, cyber-attacks continuously penetrate companies’ system. 74% of organizations admit that remote working is a major factor that contributes to increased digital risk.
How Cyber Criminals Can Still Break Through the 2FA System
While MFA and 2FA are seen as a solution for access breach, one must remember that not all MFAs are created equally. To better comprehend how different the process can be for different MFAs, let’s imagine yourself as a user in his/her daily work life. You are currently working as a junior sales employee. This morning, you need to access Salesforce system, which is protected with SMS-based OTP for 2FA.
You open your laptop and ready to log in with your username and password. You reach the secret notes with all your usernames and passwords written on it. You know that you are not supposed to write them down. But with dozens of apps you have to open every day and different passwords to manage, it’s hard for you to keep up with it. Afterall, creating a strong password is not that easy. You have to use a combination of capital letters, numbers and symbols and you are told not to use the same password in different apps to minimize credential hacks.
After taking a look at your secret notes, you log into the device and access the system. The authentication flow should work like this:
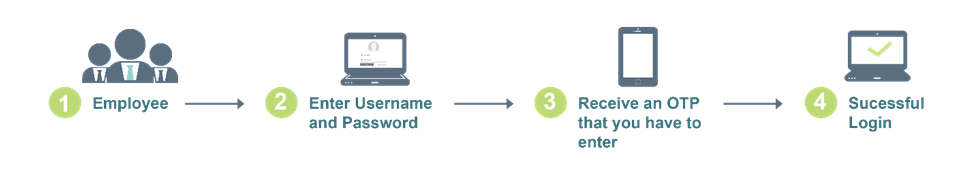
When you finish with this login, navigate to other apps, and get back to the Salesforce system later that day, you will have to repeat the process again. You will have to enter an OTP every single time. Sometimes there’s a delay with the OTP and you are run out of time allowed to enter the OTP.
Later that afternoon, you have done with your work and decide to take a little break before going home. But, hey! There’s an email from the IT department. It reminds you to change passwords frequently to minimize password hacking possibility. After a full day of work, you feel exhausted. Changing your password (again) is the last thing on your mind right now. But still, you want to comply with the IT rules. Afterall, it is for the company’s data safety.
You scramble your desk to find the secret notes. It is the one with your usernames and passwords written all over it. But, it is nowhere to be seen. You are now beginning to panic. You try to login using the combination of passwords that might be possible. But none is working. As a last resort, you email the IT department and ask for a password reset. It has been the second time this month. Sounds familiar?
In addition to being a ‘hassle’, an SMS-based OTP authentication is not ideal to implement. Modern phishing attacks can intercept username and password combo, as well as the OTP.A hacker may send you a fake request with authentic looking email, asking you to click a link and log into your Gmail account like normal. You follow the instruction, thinking that the request is legitimate. Except that you are wrong.
A modern phishing scheme beats mobile based authentication by sending a phishing email with a link that directs you to a fake login page that resembles a lot with the real website. Let’s take a look at how a phishing works although you are using an SMS-based OTP for 2FA.
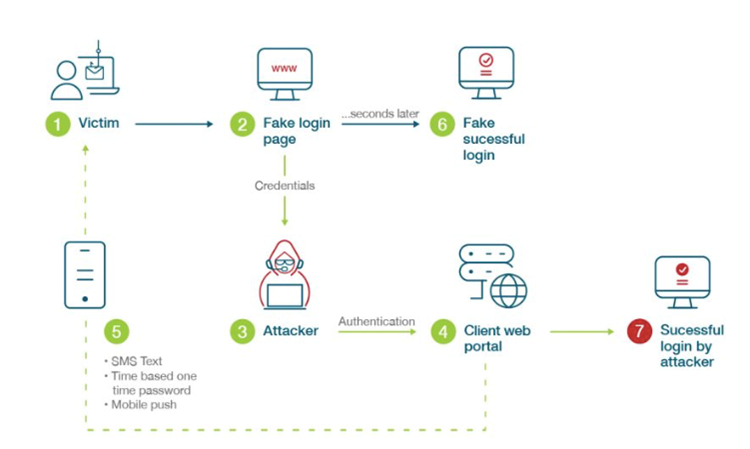
After stealing your OTP with a fake website login, the attacker will be able to log into the real website using the OTP information you have sent them. Only 76% of cyber-attacks can be blocked using SMS-based OTP.
How YubiKey Can Turn Your Work Life For the Better
Now, let’s re-imagine the same scenario with YubiKey instead. This time, you log into the Salesforce system by simply plugging it into your USB port and touching the button. You might also choose to tap it against your phone for NFC authentication on the go. This time, you won’t need to remember the password. Voila! Now you access the system quickly and easily. Instead of wasting your precious time with username and password, now you can focus on what you do best – selling your products!
YubiKey works based on modern authentication protocols and offers high level of security. Because of its nature as hardware authentication, YubiKey is not susceptible to remote attack. YubiKey generates public and private key when it tries to access a service. Once YubiKey is used in a service or apps, the generated private key is bound to the original URL/IP so cyber criminals cannot use it in a fake website.
YubiKey also requires user presence, which means that it will require a user that physically access and verify the entry. The touch sensor in YubiKey verifies that a real person is using the key, not a trojan or hacker. YubiKey is also flexible to use in multi authentication protocols. With more than 700 applications to support, you can secure your authentication system with strong 2FA, MFA, and passwordless authentication.











