Nov 26, 2024 | Uncategorized
The NIS 2 Directive represents a pivotal advancement in enhancing cybersecurity within the European Union, targeting sectors essential to societal and economic operations. Effective October 17, 2024, the directive mandates stringent security measures for companies,...
Nov 26, 2024 | Articles, Articles, Articles, Articles
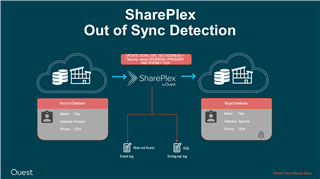
Introduction SharePlex users often inquire about how the tool detects, processes, and resolves discrepancies between rows in source and target databases. SharePlex is specifically designed to maintain synchronization in replication streams, addressing cases where the...

Nov 7, 2024 | Uncategorized
It’s no coincidence that Graylog 6.1 is making its debut right before Halloween. This release is a true powerhouse, designed to address some of the most enduring and complex challenges in Security Information and Event Management (SIEM). With a suite of innovative...

Nov 4, 2024 | Uncategorized
In today’s fast-paced cybersecurity landscape, combating sophisticated threats requires innovative tools that provide deep insights. One such powerful tool is NetFlow—a technology that unlocks valuable network traffic data to help organizations safeguard their...