News & Events
Where does data destruction fit in the IIoT
Fifteen years ago, the concept of a “computer” was much simpler—limited to desktops, basic mobile phones, and other standard devices. Today, the Internet of Things (IoT) has drastically expanded that definition, embedding processing power and data storage in everything from smartphones to smart vehicles. However, this evolution has also introduced new security challenges. Unlike traditional IT devices, Industrial IoT (IIoT) hardware is designed to endure harsh environments, making data destruction more critical. As these devices store valuable data, robust data destruction methods must be employed to prevent unauthorized access.
What is Your Definition of Insider Threat?
How you define insider threat is critical, because how the problem is defined will drive how you define and implement the solution.
Key Features of NetFlow Optimizer
NetFlow Optimizer offers powerful capabilities tailored for network administrators and security professionals. It empowers organizations to fully leverage NetFlow data, enhancing network security and IT operations. Whether focusing on proactive network traffic monitoring or ensuring top-notch security, these key features provide essential tools to meet your needs effectively.
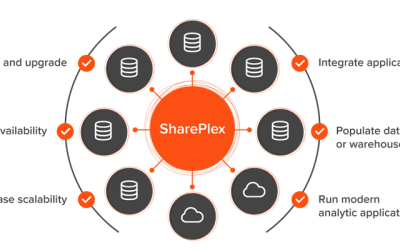
What is dynamic data movement?
Dynamic data movement involves replicating data from traditional RDBMS systems like Oracle to other databases such as MySQL, Azure SQL Database, Kafka, and PostgreSQL.
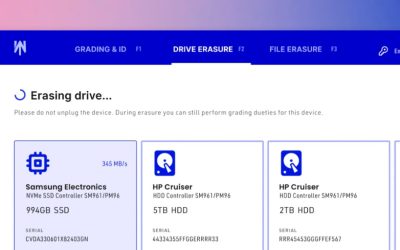
Let’s Discuss Data Sanitization: Misconceptions, Misinformation, Reality.
In the digital age, concerns about data management and privacy are rapidly growing as the volume of data increases exponentially. With regulatory compliance and data privacy issues becoming more prominent, it is the responsibility of the IT industry to ensure data security and prevent leaks by implementing proper data sanitization procedures and tools.
Risks of Windows Autoplay
When convenience outweighs caution, features designed to enhance user experience can become vulnerabilities. Windows Autoplay is a prime example. While it instantly launches applications or media from external devices, its design can pose significant security risks.
Different types of APIs explained: styles, protocols, audiences + real-life examples
Depending on how you categorize them, APIs come in several different types, each with its own scope, benefits, and target audience. This makes them uniquely suited for different purposes.
CISOs Navigating the GenAI Tide: Actionable Insights from SANS Institute
The widespread adoption of Generative AI (GenAI) is revolutionizing industries, driving unprecedented innovation and efficiency. However, this technological leap introduces significant cybersecurity challenges. SAP, a global leader in enterprise software, has outlined its comprehensive approach to GenAI cybersecurity, offering crucial insights for Chief Information Security Officers (CISOs) and security professionals. Leveraging SAP’s strategic framework, the SANS Institute presents five actionable cybersecurity considerations to navigate the GenAI landscape effectively.
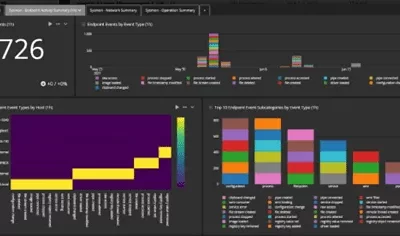
Security Awareness and Log Management for Security Analysts
In today’s remote working environment, security professionals need specialized technical security awareness education that goes beyond the standard “don’t click a phishing link” training provided to the rest of the company. While security analysts are adept at recognizing phishing emails and setting secure passwords, their cybersecurity awareness must extend to optimizing log management strategies to keep pace with evolving threat actors.
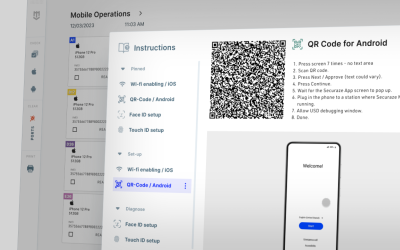
Boosting Your Business: The Power of Smartphone Refurbishing with Securaze Mobile
Securaze Mobile has long been a trusted name in secure data erasure for the mobile industry. In our ongoing quest for innovation, we are thrilled to unveil the newest developments in Securaze Mobile, ushering in a new era of secure mobile device management.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065