News & Events
TRANSITIONING TOWARDS A PASSWORDLESS ERA
HOSTED BY : SSH , SIAM BC & DTASIA
TUESDAY MAY 16, 2023 • 1 : 15 PM THE ST . REGIS BANG KOK HOTEL
159 Rajadamri Road, Khwaeng Lumphini, Pathum Wan, Bangkok 10330, Thailand
Bonding trip @ ClubMed
Our recent company bonding trip @ ClubMed on 4-6 May was a huge success!
Summary of the Investigation Related to CVE-2023-0669
We’d like to provide an update on our investigation into the suspicious activity detected in our Fortra GoAnywhere MFT solution. Working with Unit 42, we have completed our investigation and have compiled a factual summary of the investigation, as well as continuous improvement actions Fortra is taking to further strengthen our systems and recommended actions customers can take to secure their data and improve their security posture using available features in the GoAnywhere MFT solution.
Syslog-ng 101, part 7: Networking
This is the seventh part of my syslog-ng tutorial. Last time, we learned about syslog-ng destinations and the log path. Today, we learn about syslog-ng network logging. At the end of the session, we will send test messages to a syslog-ng network source.
Security Awareness Training ROI: Part 2 Of 3
If you haven’t read Part 1 of our Security Awareness Training ROI, you can here. In it, we discussed the high-level overview of why security awareness training should be a vital part of any company’s cybersecurity strategy and how to get the best security awareness training ROI.
Open-Source SSH: When Free Is Not Free
Free software, also known as open-source software, sounds like a good way to cut already high IT costs. As the name suggests, it’s free, thus it shouldn’t cost anything. But is it really that simple? Let’s find out.
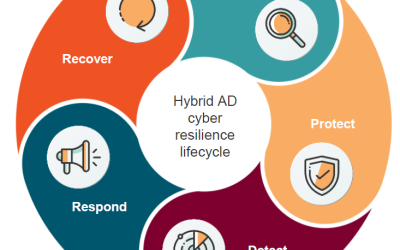
Active Directory Cyber Resiliency
Reduce Cyber Risk for your organization
In 2021, 25 billion attacks on Azure AD accounts were reported. Your organization Active Directory (AD) security sits as your organization’s cornerstone, but it’s also every cyber villain’s favorite target whom can control your AD and then your entire enterprise.
Syslog-ng 101, part 6: Destinations and log path
This is the sixth part of my syslog-ng tutorial. Last time, we learned about syslog-ng source definitions and how to check the syslog-ng version. Today, we learn about syslog-ng destinations and the log path. At the end of the session, we will also perform a quick syntax check.
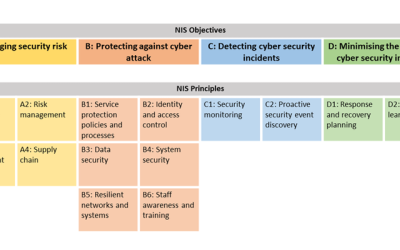
Attackers keep trying, but NCSC’s CAF guidance will keep Active Directory protected
As an IT professional, it shouldn’t surprise you to know that there are 95 million attempted Active Directory (AD) attacks every day. But cyberattack concerns aren’t limited to on-premises Active Directory. In fact, last year, there were more than 25 billion attacks in Azure AD.
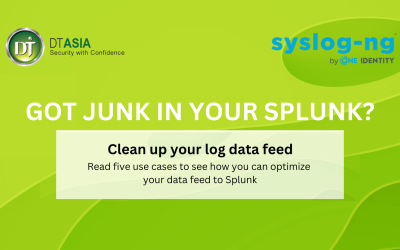
White Paper: How to configure syslog-ng™ PE to cooperate with Splunk
Splunk is a popular search and analysis platform. Many users of Splunk also have syslog-ng™ deployed in their environments. This guideline describes scenarios in which Splunk users can benefit from syslog-ng™ Premium Edition features and offers some technical guidance to optimize the syslog-ng™ configuration.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065