News & Events
Benefits of NetFlow Optimizer
NetFlow data is essential for enhancing network security and streamlining IT operations. It provides a detailed view of network traffic, enabling organizations to proactively detect security threats, monitor user activity, and gather valuable insights for effective network management and optimization. With comprehensive visibility into network traffic patterns, NetFlow data empowers security teams and IT operations to maintain a robust and secure network environment while boosting the overall performance and efficiency of the network infrastructure.
What to consider when replicating data to the cloud
Replicating data into the cloud offers numerous advantages for organizations, enhancing their data management strategies and overall efficiency. Here are the key benefits:
Why use a http()-based destination in syslog-ng?
Logging has evolved significantly from the traditional syslog days. Despite this, many syslog-ng users continue to rely on syslog protocols for log transport and flat files for log storage. While most SIEMs and log analytics tools can receive syslog messages or read them using their agents, you can often leverage the http() destination of syslog-ng to send logs. This method offers high performance and a simpler architecture to maintain.
MOST INSIDER DATA LEAKS ARE ACCIDENTAL
Data breaches are becoming alarmingly common, with many high-profile cases involving malicious actors like ransomware gangs or disgruntled employees. These cyberattacks often target large companies, demanding ransom amounts that can reach millions of dollars. Unfortunately, even when companies pay, it rarely guarantees the restoration of their data. This highlights the serious threat posed by cybercriminals exploiting technological vulnerabilities, leading to significant impacts on both employee and customer data. Beyond media headlines, it’s crucial to understand the mechanisms and true costs of data breaches.
API monetization models: Strategies to leverage APIs for greater revenue
API monetization models showcase strategies and tactics for using APIs to generate revenue, impacting the bottom line both directly and indirectly.
A Tale of the Three *ishings: Part 3 – What is Vishing?
Over the past two decades, the security industry has made significant strides in using technology to secure technological assets. However, the human factor in cybersecurity often remains overlooked. Consequently, cyber attackers have shifted their focus from targeting technology to targeting people. Among the various methods they employ, the three most common are phishing, smishing, and vishing. This blog series delves into these methods, the tactics and techniques used by cyber attackers, and how you can protect yourself.
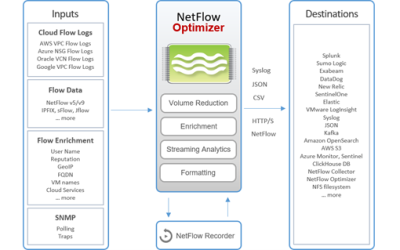
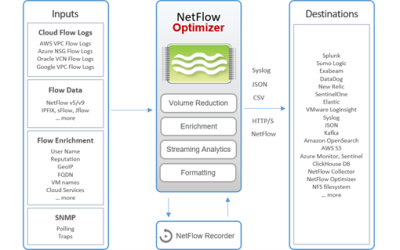
NetFlow Optimizer
NetFlow Optimizer™ (NFO) is a software-only processing engine for network flow data. It accepts NetFlow, IPFIX, sFlow, J-Flow from network devices (routers, switches, firewalls, virtual networks), and Cloud Flow Logs (AWS VPC, Microsoft Azure, Oracle OCI, and Google VPC). It provides real-time network monitoring and enables advanced level of operational intelligence and security for virtual and physical networks.
Crucial backup strategies to defend against ransomware attacks
Ransomware payouts are trending back up. According to Chainalysis, a cryptocurrency tracing firm, 2021 was a record year for ransomware payments, totaling almost $1 billion. In 2022, there was a drop, but in 2023, ransomware payouts returned to that same torrid pace with an estimated $900 million in payments. This rise in ransomware activity can be attributed to the ramping up of ransomware group operations and a surge in extortion efforts. To avoid becoming a victim and defend against ransomware threats, you need a strong backup plan that takes into account the many ways that attackers can infiltrate your network.
Work Diagnostics
Introducing Work Diagnostics, an integral component of the Securaze Work software suite tailored for comprehensive testing of technical device functionalities. This diagnostic tool enhances report quality, bolsters the authenticity of Securaze products, and facilitates the efficient categorization of reusable and resalable items. Empowered with Work Diagnostics, users gain a meticulous overview of their assets, enabling informed decisions regarding repair, sale, or disposal with projected revenue considerations. Purchasers of pre-owned items benefit from a certification affirming equipment status, instilling confidence and reliability.
syslog-ng Store Box Splunk/HEC and Sentinel destinations
The syslog-ng Store Box (SSB) appliance, built on syslog-ng Premium Edition (PE), offers a user-friendly graphical interface while retaining most of syslog-ng PE’s robust features. A key application of SSB and syslog-ng PE is enhancing the logging infrastructure for SIEM/log analysis. Notably, SSB has recently added support for log analytics destinations like Splunk HEC (HTTP Event Collector) and Microsoft Sentinel.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065