This post is also available in:
 Vietnamese
Vietnamese
Protecting Your Most Valuable Assets
Company’s information is increasingly considered as key corporate assets. Customers’ information, financial data, important documents and product blueprints are examples of important and sensitive data that must be guarded from unauthorized access to maintain information security.When it is not properly managed, your company’s critical data may turn into liability rather than asset.A survey in 2021 stated that the average total cost of data breach reaches up to $4.24 million with 80% of data breaches are connected with compromised privilege credentials in the form of users, passwords, tokens, or certificates.
Privilege credentials are described as credentials that provide elevated access and permissions across accounts, applications, and systems. Although they are previously commonly identified as IT admins, the definitions of privilege users are now expanding. Using the new definition, your corporate key users such as HRD or Financial Manager can also be given privilege credentials. It may even be given to someone from outside of your organizations, such as contractors or temporary and contract employees who are allowed to access your most sensitive data within a defined time frame. With the increasing number of privilege users, managing your company’s privilege accounts is more important than ever. Privilege Access Management is critical, as these users are prime target for cyber criminals. Yubikey ensures that all privilege users are highly secured, protecting the company from illegal account takeovers.
How To Set Your Company’s Privilege Access Management (PAM)
Privilege Access Management is a solution to ensure your data security by using a range of tools that allows you to retain control of critical information. The best practice to strengthen your access security is adding layers of security from the least privilege users. Users should have different levels of privilege based on what they are required to see and do in your system.
PAM requires separating individuals with privilege access in a secure repository. Once isolated, these privilege users are required to go through your PAM system to gain access to privilege credentials- adding a layer of security to your password protocols. To have a clearer understanding on how it works, you can find the illustration below. Within each step, an elevated credential and authentication is added

Stop Phishing and Account Take Over in Their Tracks
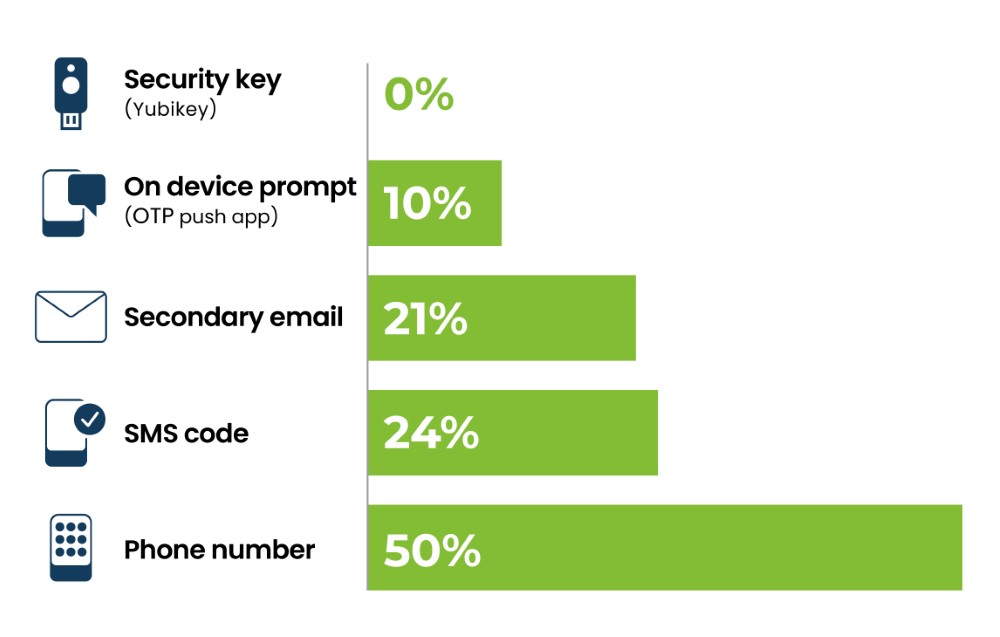
PAM usually relies on IAM for authentication, often requiring a little more than a password or legacy MFA. Although a security layer has been added, it is important to note that not all MFAs are created equally. Legacy authentication methods which employ user names, passwords, and mobile based authentication such as SMS, OTP and push notifications are still vulnerable to phishing and account takeovers. These type of authentication method will be easily breached by phishing attack, malware, man-in-the-middle attack, SIM swapping, etc.
Privilege Access Management (PAM) is critical as privilege users are the main targets for cybercriminals because of the sensitive information they possess. Yubikey ensures that all privilege users meet a higher security level, in turn protecting organizations from accounts takeover. By deploying phishing-resistant MFA such as Yubikey, you will have a 360o protection.Compared to other methods, Yubikey stops account takeovers by 100%, including bulk and targeted phishing attacks.
Why Yubikey is the Front Runner for MFA Security Key?
Yubikey works very well both in legacy and modern authentication protocols such as FIDO U2F and FIDO, as well as OTP, Smart Card and OpenPGP. Yubikey can be used as a bridge between the legacy and modern authentication systems, making it easier for you to secure your accounts without having to use too many keys.Yubikey works with leading IAM and PAM solution and can be easily integrate to 3rd party systems, including Axiad, Duo, Google Cloud, Microsoft Azure Active Directory, Okta Workforce Identity, PingID, RSA SecurID Suite and CyberArk.
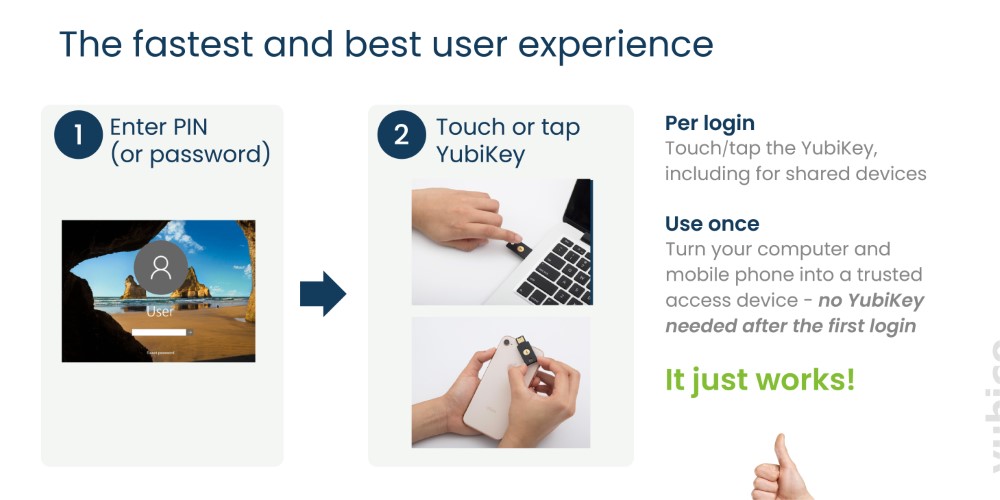
Yubikey generates both private and public key with the private keys stored in the secure element on the Yubikey. This method ensures full protection for your privilege users and data. Yubikey also requires user presence to validate that a person is physically present and in control of Yubikey. With a simple tap and go, Yubikey provides the best and the fastest user experience.
Learn more on how Yubikey can help you manage your privilege accounts.










