Jul 30, 2024 | Articles, Articles, Articles, Articles
NetFlow Optimizer offers powerful capabilities tailored for network administrators and security professionals. It empowers organizations to fully leverage NetFlow data, enhancing network security and IT operations. Whether focusing on proactive network traffic...
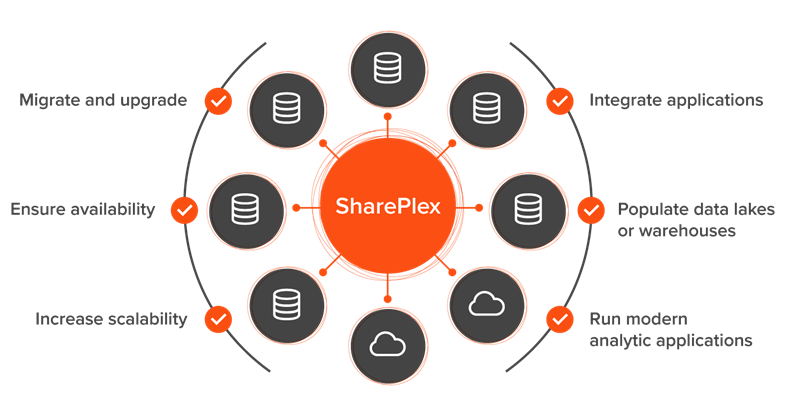
Jul 29, 2024 | Uncategorized
Dynamic data movement involves replicating data from traditional RDBMS systems like Oracle to other databases such as MySQL, Azure SQL Database, Kafka, and PostgreSQL. Data is the lifeblood of your organization, containing crucial information that drives business...

Jul 17, 2024 | Uncategorized
When convenience outweighs caution, features designed to enhance user experience can become vulnerabilities. Windows Autoplay is a prime example. While it instantly launches applications or media from external devices, its design can pose significant security risks....
Jul 15, 2024 | Uncategorized
Depending on how you categorize them, APIs come in several different types, each with its own scope, benefits, and target audience. This makes them uniquely suited for different purposes. API stands for Application Programming Interface. An API includes a collection...