News & Events
Syslog-ng development and AI
Recently, several people have asked about the syslog-ng project’s position on AI. In short, the answer is one of cautious optimism. We are open to using AI, but we do not allow it to take over any critical responsibilities from human developers. What does this approach look like in practice?
Be Prepared: Mobile Phishing Expected to Surge Fourfold During the Holiday Season
Users and organizations should expect a sharp rise in phishing activity in the coming weeks as cybercriminals take advantage of the holiday shopping rush, according to a recent report from Zimperium. The findings show that mobile phishing attacks increase by as much as four times during the festive season, with many campaigns posing as trusted brands and popular online marketplaces such as Amazon and eBay.
Backup Before It Breaks — and Wipe Before You Let Go
Recent findings from heise online have raised serious concerns about a large number of aging Western Digital hard drives, especially from the Blue, Red, and Purple series. These models use Shingled Magnetic Recording (SMR) technology — a method that increases storage capacity by overlapping data tracks like roof tiles.
Gobbling Up Insights: Graylog 7.0 Serves Up a Feast
A feast of new features. A cornucopia of new capabilities. A banquet of breakthroughs (and the T-day puns are just getting started). Graylog 7.0 brings a full plate of advancements that help security teams cut through noise, control cloud costs, and respond with confidence. We’re serving practical improvements across dashboards, automation, and AI support so analysts can focus on action instead of manual effort.
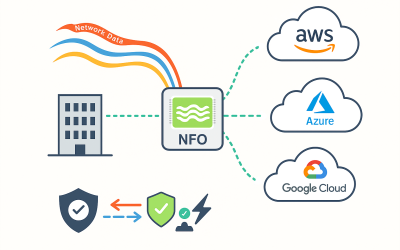
The Role of NetFlow in Cloud Security: Bridging the Visibility Gap for Hybrid and Multi-Cloud Environments
The shift to cloud computing has transformed the way enterprises build and scale their IT infrastructure. But with this transformation comes a new challenge: maintaining security and visibility across environments that span on-premise networks, public clouds, and everything in between.
Is a “Good” Monitoring Solution Good Enough?
Data is now the lifeblood of every modern organization. Ensuring the right data is available to the right people at the right time has become a strategic imperative. At the same time, businesses are under pressure to reduce costs while still enabling growth, maintaining high performance, and delivering exceptional customer experiences.
Phishing Emails Use Invisible Hyphens to Avoid Detection
A recent phishing campaign has been identified using invisible characters to sneak past email security filters, according to Jan Kopriva from the SANS Internet Storm Center.
Introducing New Capabilities: Versasec FIDO2 Enterprise (+ Video Demo)
Passwords continue to be one of the biggest drivers behind identity theft and security breaches. To reduce this risk, organizations are shifting towards passwordless authentication. FIDO2 security keys provide phishing-resistant, passwordless authentication to protect access to sensitive applications, systems, and Windows endpoints.
Benefits of SecureData Remote Management
Data breaches are increasingly common, with recent studies showing that in 2024, over 16.8 billion records were exposed due to data breaches. This equates to about 533 records compromised every second throughout the year. The alarming statistic underscores the critical need for powerful data encryption and efficient management practices. Encrypted drives are storage devices with advanced encryption algorithms, which are vital in protecting sensitive information from unauthorized access. Remote management technology enables users to securely administer these encrypted drives from any location, offering unprecedented levels of convenience.
Winners’ Circle: Quest
Quest Software is proud to receive DBTA recognition for Best Data Governance Solution (erwin Data Intelligence) and Best Database Development Solution (Quest Toad), underscoring our commitment to comprehensive data solutions that empower organizations to drive business value from their data and AI initiatives.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065