News & Events
Securing AD/LDAP Environments: How OpenOTP Leads the Way
Many European organizations face a distinct challenge: strengthening cybersecurity while complying with strict regulatory frameworks. Across industries such as banking, insurance, education, healthcare, and government, Active Directory (AD) and Lightweight Directory Access Protocol (LDAP) remain fundamental components of IT infrastructure. However, as cyber threats grow increasingly sophisticated and compliance obligations intensify, these organizations must adopt new approaches to secure their AD/LDAP environments without sacrificing operational efficiency or data sovereignty.
Sentinel: Reduce costs with syslog-ng
Organizations adopting Microsoft Sentinel have reported a 93% reduction in time required to configure and deploy new connections, with the time saved in configuration alone valued at $618,000. These gains highlight Sentinel’s flexibility and scalability. However, Sentinel’s consumption-based licensing model introduces a critical challenge: as more systems and data sources are onboarded, costs can grow rapidly, often resulting in unexpected invoice increases.
Top 7 Advantages of Passwordless Authentication for Businesses
The digital landscape continues to evolve rapidly, and so do the methods used to protect online environments. Passwordless authentication has emerged as a powerful alternative to traditional password-based security, helping organizations improve protection while simplifying access. Instead of relying on memorized passwords, users verify their identity through more secure and convenient methods.
From blueprint to business value: How to build an AI-ready data foundation
You already know the stakes.
Nearly 80% of AI initiatives fail, and the root cause is rarely the algorithms—it’s data. You’ve seen how traditional governance slows innovation, creating a trust paradox where controls increase friction instead of confidence. You understand the promise of govern-as-you-go and how quickly organizations can transform when governance becomes embedded rather than enforced.
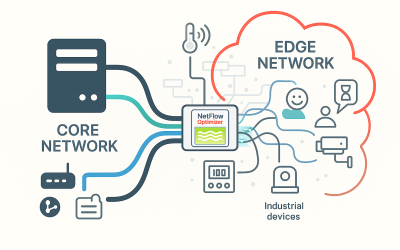
Securing the Edge: How Optimized NetFlow Solves the Visibility Problem for IoT and Industrial Networks
The modern enterprise extends far beyond the traditional data center and the employee laptop. Today’s environments include a vast array of devices operating at the network edge—ranging from smart surveillance cameras and HVAC sensors to specialized Operational Technology (OT) controllers in factories and warehouses. While this growing ecosystem of Internet of Things (IoT) and Industrial Control Systems (ICS) significantly enhances business capabilities, it also introduces a substantial and often overlooked security gap.
Is My Business Ready for Passwordless Authentication?
At Versasec, we believe security should enable efficiency and growth—not create unnecessary complexity. Today’s business environment requires far more than the outdated and fragile protection offered by passwords. This legacy approach is not only a critical security weakness, but also a significant operational burden. It’s a challenge we know well, and one we are committed to solving.
UX Best Practices for Passkeys: Understanding Device-Initiated Authentication
Passkeys are different from traditional username-based approaches to passwordless sign-in and MFA. This article explains how to design the most effective passkey experience for users, with a focus on web browsers as the platform.
Versasec Accelerates High-Assurance MFA and Passkey Adoption with Yubico FIDO Pre-reg
Versasec has announced the integration of Yubico FIDO Pre-reg with Versasec vSEC:CMS and vSEC:CLOUD, enabling enterprises to achieve full lifecycle management and simplify onboarding through the delivery of pre-enrolled YubiKeys to end users. This critical integration aims to accelerate adoption while significantly enhancing the security of multi-factor authentication (MFA) and device-bound passkeys.
The Hidden Risk of Synced Passkeys: Why FIDO2 Device-Bound Passkeys are the Secure Choice
In cybersecurity, convenience often comes at a cost. Synced passkeys—touted for their ability to work seamlessly across multiple devices—are a prime example. While they simplify access, recent research shows they can introduce serious vulnerabilities, potentially exposing entire organizations to risk.
Defend Against Cyber Threats With Encrypted Drives
Cyberattacks are increasing in both scale and complexity, making data protection one of the most critical challenges facing organizations today. While traditional security controls — such as firewalls, antivirus software, and network monitoring — continue to play an essential role, they are no longer enough on their own.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065