
If you’re a gamer of a certain generation, you probably remember the arcade classic Asteroids. You piloted a tiny triangular ship, dodging and shooting incoming space rocks that started slow but gradually sped up. Success required rapid decision-making—figuring out which rocks posed a real threat and which you could afford to ignore.
Triage in cybersecurity is much the same. With threats constantly flying in from all directions, you need a structured way to determine which incidents demand immediate attention and which can wait. Not every alert signals disaster, and without effective triage, security teams risk being overwhelmed by noise, wasting time, and missing real threats.
What Is Triage in Cybersecurity?
In cybersecurity, triage is the process of assessing and prioritizing security incidents based on impact and urgency. It helps security operations centers (SOCs) respond faster and smarter by focusing on what matters most.
The triage process typically involves:
-
Initial Assessment – Quickly review the alert for severity, potential impact, and likelihood of escalation.
-
Threat Intelligence Correlation – Match the incident with known threat data to validate its relevance.
-
Criteria-Based Prioritization – Use predefined standards to categorize incidents and determine response urgency.
Common Priority Levels:
-
High – Requires immediate response.
-
Medium – Needs attention within 24 hours.
-
Low – Monitor with no urgent action.
How Triage Fits into the Incident Response Process
Triaging is not just about filtering noise—it’s the backbone of an effective incident response (IR) strategy. Here’s how it works:
1. Detect and Report
Monitor systems for anomalies and generate initial incident reports. A strong detection strategy highlights abnormal behavior and identifies which assets may be compromised.
2. Assess and Categorize
Evaluate incidents based on:
-
Functional Impact – How critical services are affected.
-
Information Impact – Confidentiality, integrity, and availability of data.
-
Recoverability – Time and resources required for full recovery.
Functional Impact Categories:
-
None – All services remain fully available.
-
Low – Critical services available but inefficient.
-
Medium – Some users lose access to critical services.
-
High – All users lose access to critical services.
3. Prioritize Incidents
Use impact and severity to determine urgency. Prioritization helps reduce alert fatigue by ensuring teams focus on real threats.
4. Allocate Resources
Assign staff based on incident priority and required expertise. This ensures the most qualified people handle the most serious threats.
5. Investigate
Begin root cause analysis by collecting indicators of compromise (IoCs), such as:
-
IP addresses
-
User accounts
-
Hostnames
-
Network traffic
6. Communicate and Coordinate
Incident response requires collaboration. Security, IT, and business teams must stay aligned through real-time updates and shared tools.
Challenges in Alert Triage
Even with a structured process, triage isn’t always easy. Security teams often face:
-
False Positives – Alerts that don’t reflect real incidents.
-
Alert Fatigue – Too many meaningless alerts cause real ones to be missed.
-
Human Error – Manual prioritization can lead to mistakes.
-
Immature AI/ML Models – Poorly trained models misclassify alerts or add noise.
Benefits of Effective Triage
A well-executed triage process brings measurable advantages:
-
Efficiency – Quickly zero in on threats that matter.
-
Reduced Alert Fatigue – Fewer false positives distract analysts.
-
Stronger Decisions – More context means faster, better responses.
-
Proactive Defense – Early threat identification limits damage.
Best Practices for Improving Incident Response Triage
To strengthen your triage process, consider the following:
Centralize Security Activities
Use a unified platform for all incident response tasks. Centralization improves coordination, speeds up decision-making, and ensures consistent documentation for compliance.
Use Security-Focused AI/ML
Generic AI won’t cut it. Choose analytics tools trained specifically on cybersecurity data. Look for models that:
-
Understand baseline behavior
-
Detect anomalies via behavioral analysis
-
Generate alerts based on configurable thresholds
-
Provide an anomaly index to guide triage
Implement Risk Scoring
Assign quantitative risk scores to both:
-
Events – To decide if an investigation is needed
-
Assets – To evaluate vulnerability and potential impact on critical systems
Map Detections to Attack Tactics
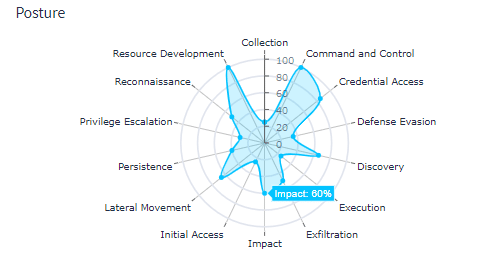
Map your detections—such as Sigma rules—to frameworks like MITRE ATT&CK. This helps identify high-impact incidents and improves situational awareness.
Use Generative AI for Context and Summarization
Generative AI (GenAI) can help summarize large volumes of log data, making it easier to spot patterns and generate action-ready reports. While it’s not meant for anomaly detection, it’s powerful for transforming raw data into actionable insights.
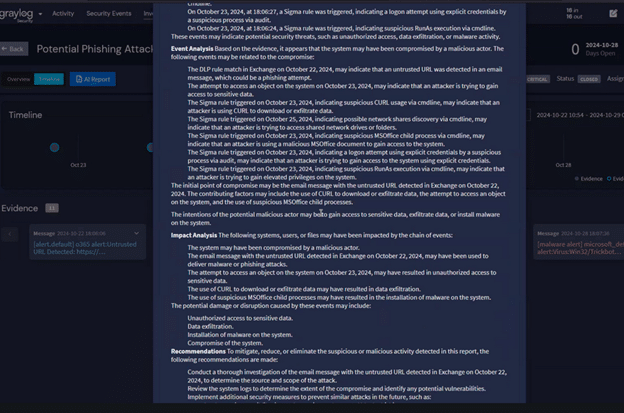
How Graylog Security Helps
Graylog Security streamlines and strengthens your alert triage process. With Illuminate content bundles, you gain access to curated Sigma rules and threat intelligence mapped to the MITRE ATT&CK framework—right out of the box.
Key Benefits:
-
AI-Powered Anomaly Detection – ML models learn over time and adjust to your environment.
-
Fast, Scalable Search – Investigate terabytes of log data in milliseconds.
-
Intuitive UI – Quickly understand and act on alerts.
-
Advanced Risk Scoring – Prioritize threats by asset criticality and event severity.
With Graylog Security, your team can respond faster, reduce alert fatigue, and maintain a strong security posture.
About DT Asia
DT Asia began in 2007 with a clear mission to build the market entry for various pioneering IT security solutions from the US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around the Asia Pacific to better understand the markets and deliver localised solutions.
How we help
If you need to know more about The Importance of Triage in Incident Response, you’re in the right place, we’re here to help! DTA is Quest Software’s distributor, especially in Singapore and Asia, our technicians have deep experience on the product and relevant technologies you can always trust, we provide this product’s turnkey solutions, including consultation, deployment, and maintenance service.
Click here and here and here to know more: https://dtasiagroup.com/graylog/










