Our Solutions
We provide solutions covering key areas of the Cybersecurity Landscape
Our Services
Solution Design & Architecture

Preventive Maintenance
Technology Deployment
Hardware Spares

24/7 Support

Online & On-site Support
Our Vendors
Our solutions are sourced from the US, Europe and Asia.
Each solution is ingested and packaged for our customers, which include
top government organisations as well as global corporations.
News & Events
Business Intelligence and Log management – Opportunities and challenges
Business intelligence (BI) is all about making sense of huge amounts of data to extract meaningful and actionable insights out of it. Log management tools such as Graylog, instead, are the perfect solution to streamline data collection and analysis, so it’s easy to understand how these two technologies can make sense when they’re coupled together.
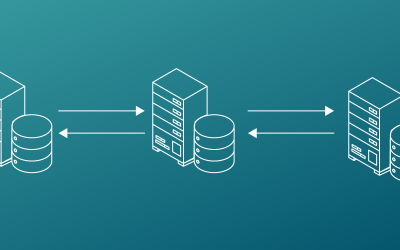
Data replication: What is it and what are the advantages of using it?
Data replication has moved from “nice to have” to “mainstream” for use cases such as High Availability and Disaster Recovery. At the same time, companies are discovering the need to replicate or move data for other reasons, including performance and translating transactional data into events.
Getting data to Splunk
Getting data into Splunk can be challenging, especially when dealing with syslog, one of the most crucial data sources. Syslog can present several hard-to-solve problems, such as high volume, non-compliant messages, and the use of the unreliable UDP network protocol. One Identity’s syslog-ng Premium Edition (PE) and syslog-ng Store Box (SSB) can help manage these challenges effectively.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065