
Sep 2, 2025 | Articles, Articles, Articles, Articles
For IT and security teams, the pressure to manage vast amounts of log and event data has never been greater. As digital environments expand and threats evolve, the need for reliable visibility and actionable insights is more urgent than ever. Yet, many organizations...
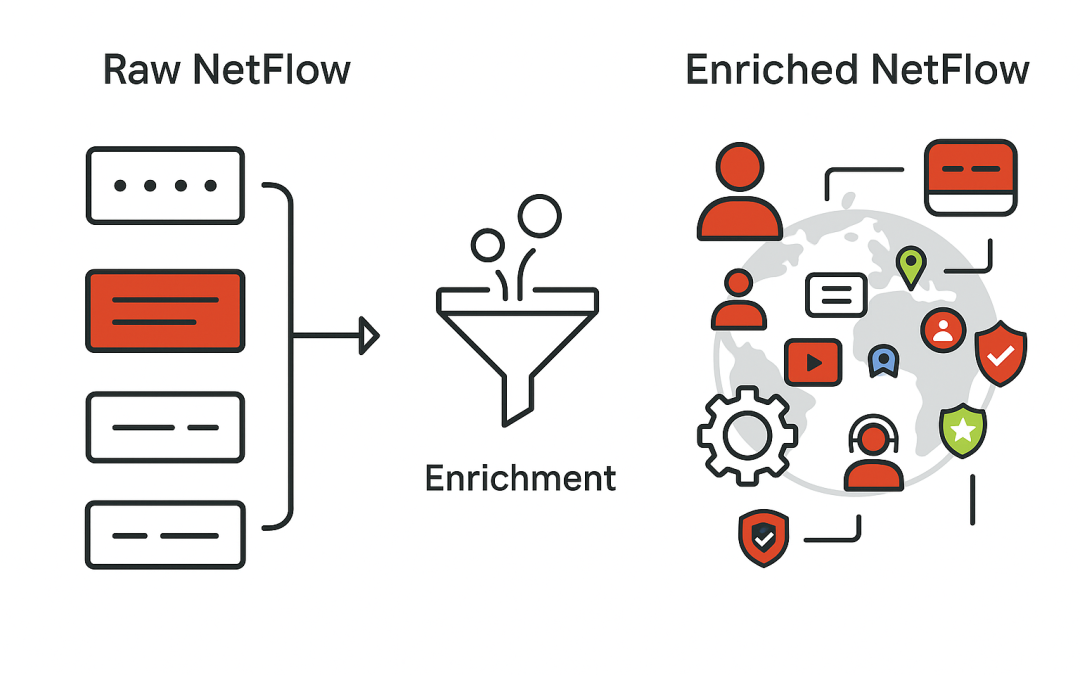
Aug 25, 2025 | Uncategorized
In today’s fast-evolving digital landscape, simply monitoring your network is no longer enough. Traditional tools may confirm whether devices are up or down, but they fall short in delivering the actionable insights needed to understand network behavior, resolve...

Aug 18, 2025 | Uncategorized
KnowBe4 Empowers Organizations to Transform Human Risk Management with AI-Driven Innovations KnowBe4, the global leader in cybersecurity and human risk management (HRM), is celebrating the success of its customers who have achieved groundbreaking results in...
Aug 12, 2025 | Uncategorized
We’re thrilled to introduce Versasec’s latest resource: “5 Reasons for Choosing vSEC:CMS for Passkey Deployment.”As organizations move toward passwordless authentication and adopt modern security frameworks, vSEC:CMS stands out as the ultimate solution for...
















