Sep 8, 2025 | Uncategorized
Data breaches are increasingly common, with recent studies showing that in 2024, over 16.8 billion records were exposed due to data breaches. This equates to about 533 records compromised every second throughout the year. The alarming statistic underscores the...

Sep 4, 2025 | Uncategorized
Quest Software is proud to receive DBTA recognition for Best Data Governance Solution (erwin Data Intelligence) and Best Database Development Solution (Quest Toad), underscoring our commitment to comprehensive data solutions that empower organizations to drive...

Sep 2, 2025 | Articles, Articles, Articles, Articles
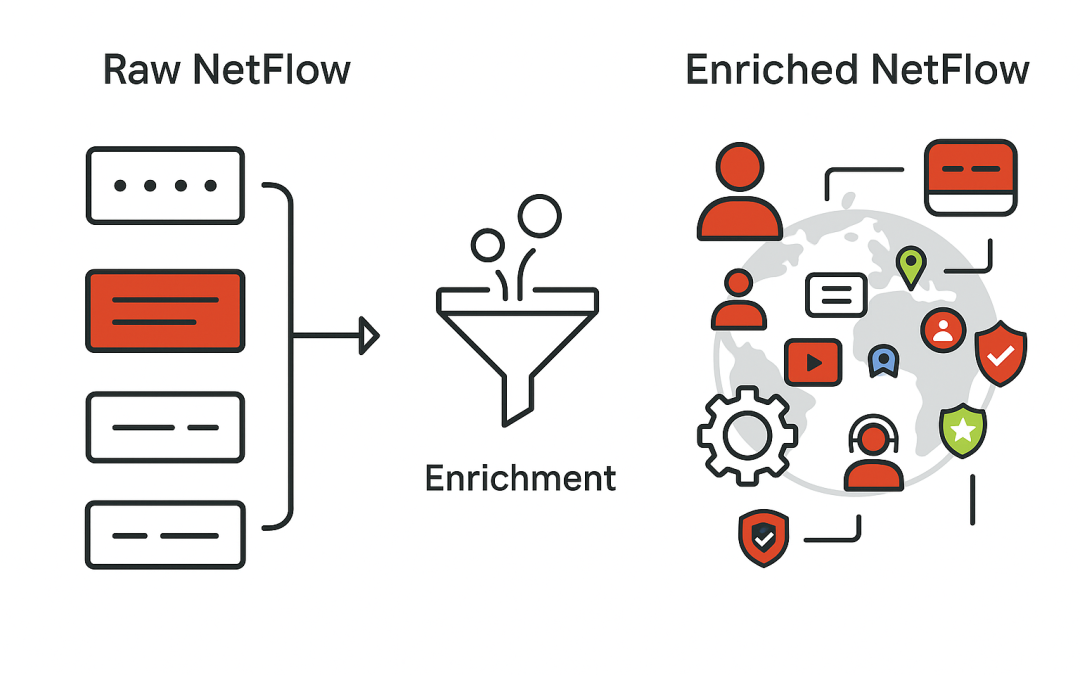
For IT and security teams, the pressure to manage vast amounts of log and event data has never been greater. As digital environments expand and threats evolve, the need for reliable visibility and actionable insights is more urgent than ever. Yet, many organizations...

Aug 18, 2025 | Uncategorized
KnowBe4 Empowers Organizations to Transform Human Risk Management with AI-Driven Innovations KnowBe4, the global leader in cybersecurity and human risk management (HRM), is celebrating the success of its customers who have achieved groundbreaking results in...