Mar 21, 2023 | Uncategorized
Helsinki, Finland – March 16, 2023 – The US federal government has shown significant interest in Quantum-Safe communications during 2022, most evidently through Quantum Cybersecurity Preparedness Act, which mandates all electronic communications to be...
Mar 21, 2023 | Articles, Articles, Articles
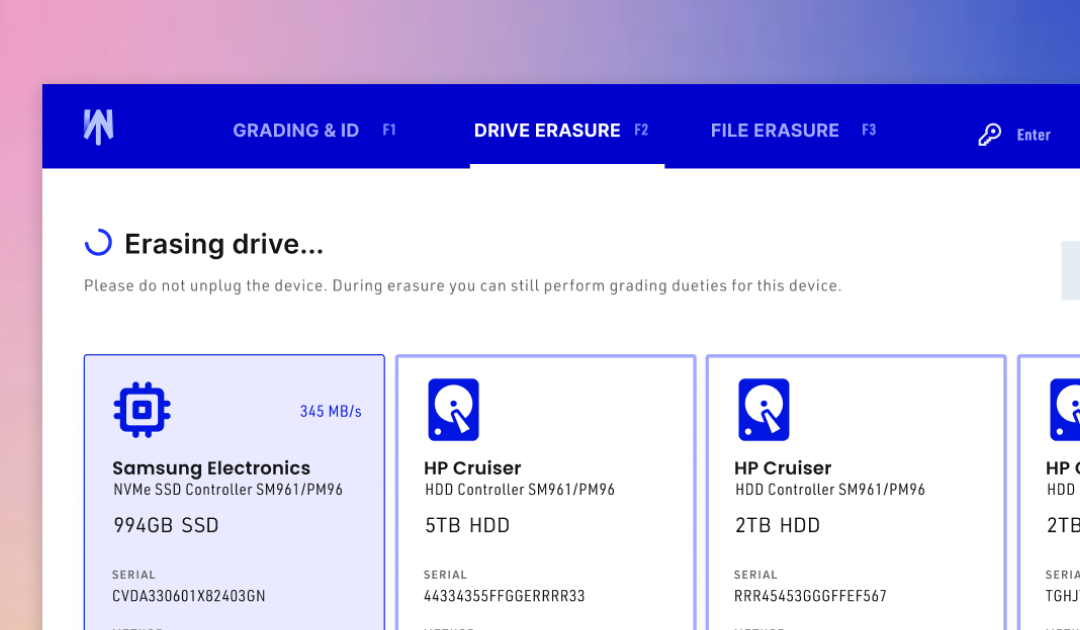
In the digital age, concerns about data management and privacy are ever-increasing as the volume of data is increasing exponentially. As regulatory compliance and concerns about data privacy grow, it is the job of the IT industry to ensure data security, preventing...

Mar 17, 2023 | Uncategorized
Compliance mandates require many of our customers in regulated industries or in high-risk environments to prove adequate levels of protection for their data, no matter where it lives or travels. This is why we’ve continued to enhance the capabilities of both the...