
Dec 8, 2025 | Uncategorized
Recently, several people have asked about the syslog-ng project’s position on AI. In short, the answer is one of cautious optimism. We are open to using AI, but we do not allow it to take over any critical responsibilities from human developers. What does this...

Dec 1, 2025 | Uncategorized
Recent findings from heise online have raised serious concerns about a large number of aging Western Digital hard drives, especially from the Blue, Red, and Purple series. These models use Shingled Magnetic Recording (SMR) technology — a method that increases storage...

Dec 1, 2025 | Uncategorized
A feast of new features. A cornucopia of new capabilities. A banquet of breakthroughs (and the T-day puns are just getting started). Graylog 7.0 brings a full plate of advancements that help security teams cut through noise, control cloud costs, and respond with...
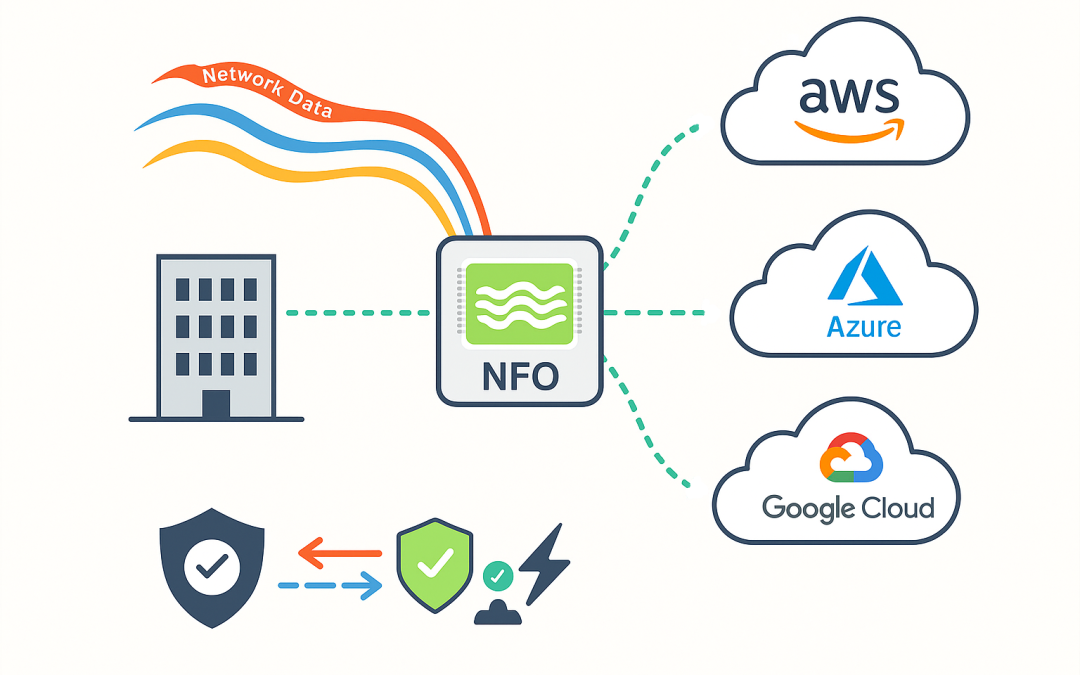
Nov 24, 2025 | Articles, Articles, Articles, Articles
The shift to cloud computing has transformed the way enterprises build and scale their IT infrastructure. But with this transformation comes a new challenge: maintaining security and visibility across environments that span on-premise networks, public clouds, and...
















