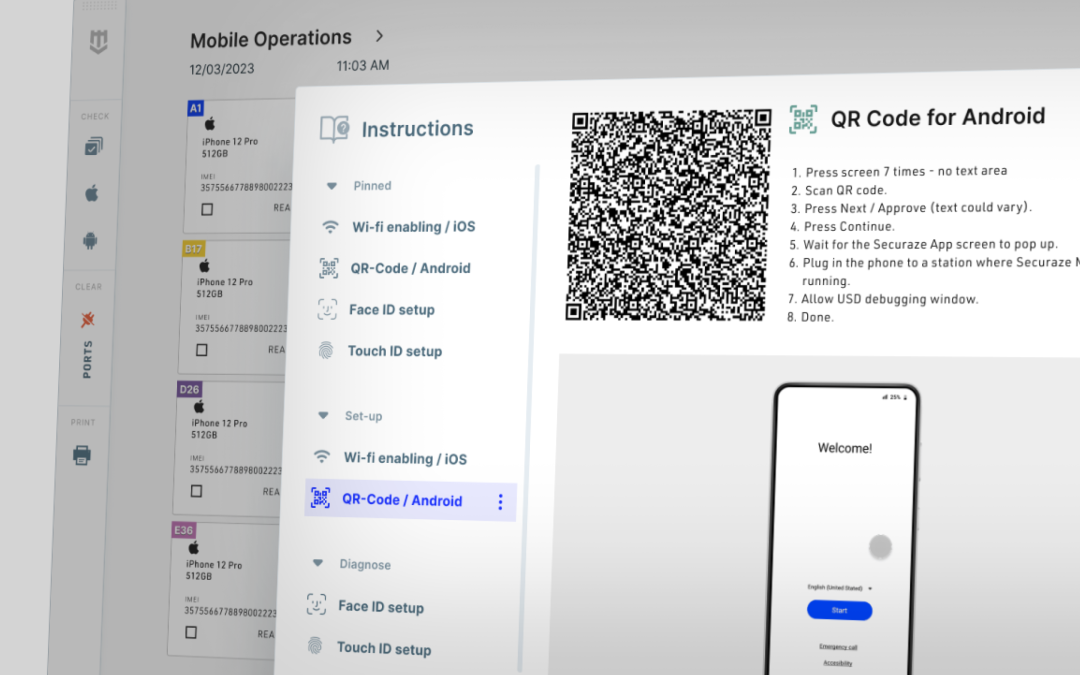
Jul 3, 2024 | Uncategorized
Securaze Mobile has long been a trusted name in secure data erasure for the mobile industry. In our ongoing quest for innovation, we are thrilled to unveil the newest developments in Securaze Mobile, ushering in a new era of secure mobile device management. In this...
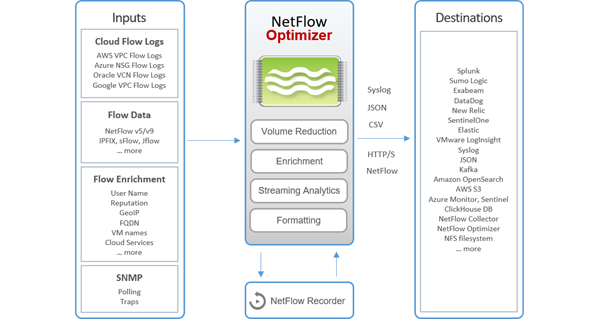
Jul 1, 2024 | Articles, Articles, Articles, Articles
NetFlow data is essential for enhancing network security and streamlining IT operations. It provides a detailed view of network traffic, enabling organizations to proactively detect security threats, monitor user activity, and gather valuable insights for effective...
Jun 27, 2024 | Uncategorized
Replicating data into the cloud offers numerous advantages for organizations, enhancing their data management strategies and overall efficiency. Here are the key benefits: Disaster Recovery and Data Resilience Cloud data replication ensures that your data is backed up...

Jun 27, 2024 | Uncategorized
Logging has evolved significantly from the traditional syslog days. Despite this, many syslog-ng users continue to rely on syslog protocols for log transport and flat files for log storage. While most SIEMs and log analytics tools can receive syslog messages or read...
















