As an IT professional, it shouldn’t surprise you to know that there are 95 million attempted Active Directory (AD) attacks every day. But cyberattack concerns aren’t limited to on-premises Active Directory. In fact, last year, there were more than 25 billion attacks in Azure AD.
The threat has become so urgent that National Cyber Security Centre (NCSC) has begun urging organisations in the UK to be increasingly critical of potential cyber threats, ensuring they have mitigation and protection measures in place. And, as attacks have transitioned from field testing of cyber weapons to infrastructure attacks as the result of the conflict in Ukraine, NCSC has reiterated these directives.
That’s why the NCSC has standardised on a framework designed to essentially be future-proof. As the result of new threats and continued attack attempts, the Cyber Assessment Framework (CAF) is structured to ensure all your bases are covered if – or rather when – an attack happens.
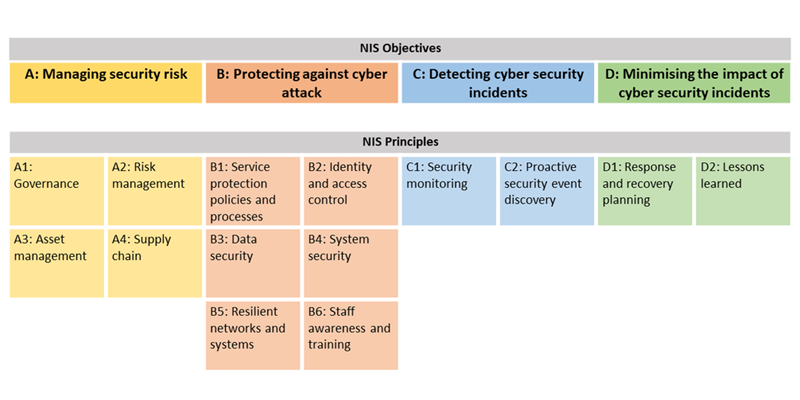
The CAF outlines four objectives to consider when building your cyber resilience strategy:
- Managing security risk
- Protecting against cyber attack
- Detecting cyber security events
- Minimising the impact of cyber security incidents
To meet the CAF guidelines requires that you fully understand the gaps that live in your infrastructure. Due to the way Active Directory and Azure AD are built, managed and supported, those gaps could potentially be vast. And very typical scenarios, like group nesting, can pose a real threat to your organisation. No one wants to find out that an attacker had gained access to their organisation through a single user and been able to escalate privileges to domain admin, for example, because of nested groups.
Worse yet, many security solution vendors take a surface-level approach to AD security; they handle it like they would any other application. The problem is, AD isn’t like any other application; it truly is the crown jewel of your environment. If SalesForce is down, a lot of people will be upset. But if AD is down, you may not even be able to get into the building to try to get a backup up and running.
At Quest, we see things differently. Our observation is that the days of a strong perimeter being enough are over. Some of the most powerful tools in an attacker’s toolbox are the people in your organisation. People make mistakes, but it only takes one for an attacker to gain entry and escalate privileges to your Tier Zero assets — your control plane.
But here at Quest, we provide a complete and continuous AD and Office 365 cyber resilience lifecycle that provides defense in depth across many layers that map to the CAF:
- Managing security risk. Minimise and manage the attack paths in your environment to limit the avenues and attacker could potentially take.
- Protecting against cyber attacks. Block attackers from making changes to critical groups, GPO settings and linking, sensitive mailboxes or exfiltrating your AD database to steal credentials – regardless of the privileges they’ve hijacked.
- Detecting cyber security events. Accelerate incident investigations with real-time auditing, anomaly detection and alerting.
- Minimising the impact of cyber security incidents. Recover AD from a scorched earth scenario and restore business operations, data integrity and customer trust in minutes or hours instead of days, weeks or months.
About DT Asia
DT Asia began in 2007 with a clear mission to build the market entry for various pioneering IT security solutions from the US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around the Asia Pacific to better understand the markets and deliver localised solutions.










