News & Events
THE IMPORTANCE OF LOG MONITORING IN ANOMALOUS BEHAVIOR ANALYTICS
Anomalous behavior analytics is one of the many advantages that big data analytics brings to the table. What role does log monitoring have in this process, and how does it work together with behavioral analytics?
9 ways to speed up your Microsoft 365 migration
Microsoft 365 migrations can be complex. With so many vital business applications in use—like Teams, OneDrive, SharePoint and Outlook along with the sheer volume of data stored on each of these—there is a lot that can go wrong.
New technology and the refurbished electronics market
While the tech world was looking forward to the upcoming release of the iPhone 15 in September, an exciting development is taking place in the market which could have a major impact on those consumers who are seeking almost-current smartphones at lower prices. The trend is the market opening up for recycling, remanufacturing and bringing back to the market used iPhone models 13 and 14.
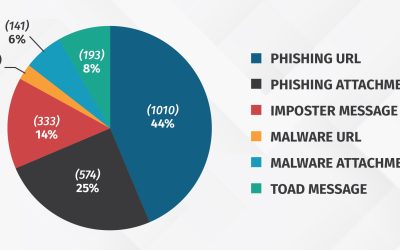
Phishing – It’s No Longer About Malware (or Even Email)
Phishing has been and continues to be one of the most common methods (TTPs) cyber attackers use because it is so effective. Phishing is a simple attack vector that enables cyber attackers to easily scale their attacks, customize for their intended targets, and bypass many security controls. Reports like the Verizon DBIR or the Microsoft Digital Defense continue to identify phishing as a top risk. While technologies like email filtering (example Proofpoint) and EDR (example Crowdstrike) make it much more difficult to succeed, cyber attackers have continued to adapt.
NEXT-LEVEL THREAT HUNTING: SHIFT YOUR SIEM FROM REACTIVE TO PROACTIVE
Threat hunting is proactively identifying and thwarting unusual network activity that could indicate an attempted security breach. It’s a historically manual activity, making it time-intensive and arduous. It’s no wonder, then, why most organizations don’t have the time, budget, or resources to undertake it effectively…if at all. That’s why many organizations rely on “reactive” threat response solutions, including firewalls, intrusion detection, and SIEM to alert analysts to an event after it occurs. Without the resources to commit to proactive threat hunting, reactive solutions are the next best option.
7 tenant-to-tenant migration planning tips
Tenant-to-tenant migrations are increasingly common. Some are necessitated by business changes like mergers, acquisitions, and divestitures, while others are driven by the desire to clean up or consolidate the IT infrastructure to facilitate business processes and reduce administrative overhead.
Getting data to Splunk
Getting data to Splunk can be challenging. Syslog is still the most important data source, and it can provide you with hard-to-solve problems (for example, like high volume, non-compliant messages, unreliable network protocol (UDP), and more). The syslog-ng Premium Edition (PE) and syslog-ng Store Box (SSB) by One Identity can make these challenges manageable.
Announcing the new SSB 4000 Appliance for Syslog-ng Store Box!
Highly secure, ultra-reliable, and enterprise grade log management.
How MFT Helps Move Large Files
What is Needed to Move Large Files?
Big files need big solutions, or rather solutions capable of reliably and securely moving files in and out of an organization. Instead of relying on free or open-sourced solutions that “might” move a big file, consider your organization’s needs around file sizes, security, encryption, compliance requirements for auditing and reporting file transfer activity, reliability, and automation. Yes, file size does matter, but it’s just one piece of the data movement puzzle for most organizations.
SSH Communications Security Launches Secure Collaboration 2024 for Secure Human-to-Human Interaction
Helsinki, Finland – September 7, 2023 – SSH Communications Security extends SSH Zero Trust Suite to a modern, real-time, secure, and audited (who did what when?) human-to-human communications platform. It consists of multiple modules helping people to share private and sensitive data in semi-interactive (email) mode and in real-time (calls, video calls, and instant messaging) and on-demand (sharing data) inside and across organizational and country borders.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065