It has been a demanding week following the latest Board of Directors meeting, where senior leadership assigned you the task of finding a suitable security analytics solution. Over the past month, you collaborated with leadership to outline basic use cases aimed at identifying a solution that aligns with both your security requirements and budget.
Your initial research has left you feeling overwhelmed by the options available on the market. While Security Information and Event Management (SIEM) tools offer extensive capabilities, they come with a hefty price tag and more power than you currently need. Moreover, their deployment typically spans six months or longer, and their specialized query languages necessitate additional team training, further elongating the timeline.
On the other hand, your centralized log management tool is already familiar to everyone in your team. With proper planning, you believe you can leverage this tool to achieve the security intelligence analytics you seek while maximizing your return on investment.
Understanding Security Intelligence
You are keen on adopting a security analytics tool but seek clarity on what exactly constitutes security intelligence.
Security intelligence provides visibility that mitigates risks through insights that enable informed decision-making. It encompasses real-time collection, normalization, correlation, and analysis of all data generated by users, applications, and environments.
If this definition sounds akin to centralized log management, that’s because it is. The right solution can deliver the necessary capabilities without the added costs associated with a full-fledged SIEM solution.
Key Components of Security Intelligence
Your centralized log management solution already excels in aggregating, parsing, normalizing, correlating, and analyzing event logs from across your environment.
Real-Time Data Ingestion
Your log management tool handles this task seamlessly day in and day out. Your IT team currently relies on it to swiftly investigate help desk tickets. Given that it also includes security event logs, leveraging centralized log management for security purposes is a logical extension.
Parsing, Normalizing, Correlating, and Analyzing Data
These tools are primarily designed to empower IT teams in effectively utilizing event logs. Their core functionality involves parsing, normalizing, correlating, and analyzing data. When applied to security event logs from your entire environment, they transform into effective security intelligence tools. A robust correlation engine within your centralized log management solution ensures you obtain the necessary data analytics for threat detection.
Integration of Threat Intelligence
Enhancing security intelligence often involves incorporating additional data sources, such as threat intelligence. This integration enables security teams to enrich their monitoring capabilities, thereby elevating your centralized log management tool to a comprehensive security intelligence solution.
Data Enrichment for High-Fidelity Alerts
By consolidating all security-related data within a single platform, you enhance the quality of alerts generated, reducing false positives. This equips your team to promptly detect, investigate, and resolve threats using a tool they are already proficient with.
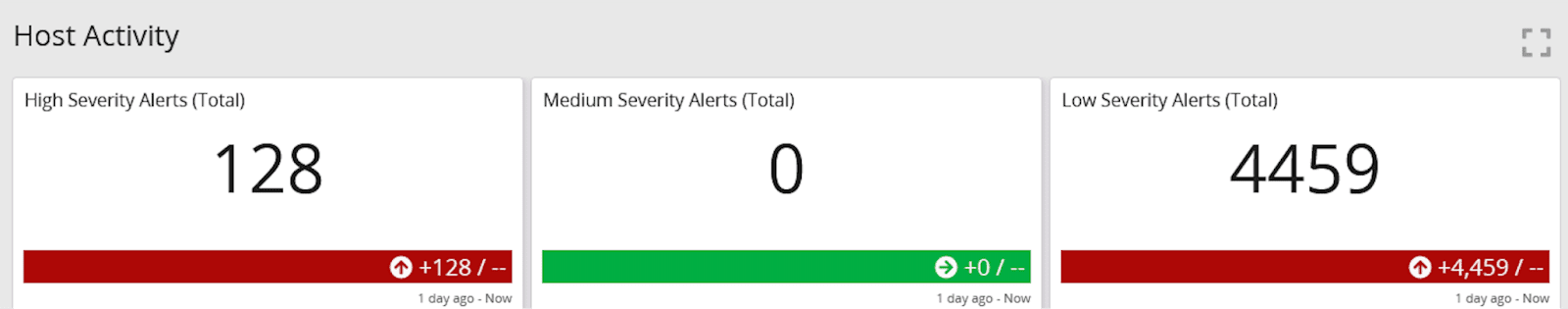
Planning Your Log Management Data Collection Strategy for Security Intelligence Analytics
When you integrate big data analytics, such as machine learning, into your security intelligence tool, you enhance its capabilities to perform security intelligence analytics. Centralized log management solutions also possess this potential. By strategically planning your log collection, you can maximize the utility of your existing tool.
Enhancing Security
To bolster your security posture, obtaining both pre-incident and post-incident visibility and documentation is crucial. Your centralized log management solution, when augmented with data analytics capabilities, facilitates this requirement. Effective collection and archival of security logs enable prompt detection of abnormal activities, thorough investigations, and comprehensive review of forensic data post-issue resolution.
As you commence planning your log collection strategy for a security analytics use case, it is essential to consider the following sources and types of data:
- Anti-Virus tools
- Endpoint Detection and Response (EDR)
- Server logs
- Firewall logs
- Network traffic
- Web proxies/Gateways
- Intrusion Detection Systems (IDS)/Intrusion Prevention Systems (IPS)
- Identity and Access Management (IAM)
- User behavior
- Threat intelligence feeds
Devops
Maturing your security posture means including your DevOps team in the process. Shifting security left by securing the Software Development Lifecycle (SDLC) means reviewing code and managing security after pushing the application to production.
As you plan your log collection strategy, you should consider the following sources and types of data:
- Application logs
- Load balancer logs
- Automation system logs
- Business logic data
- User logs
- Network activity
- Database logs
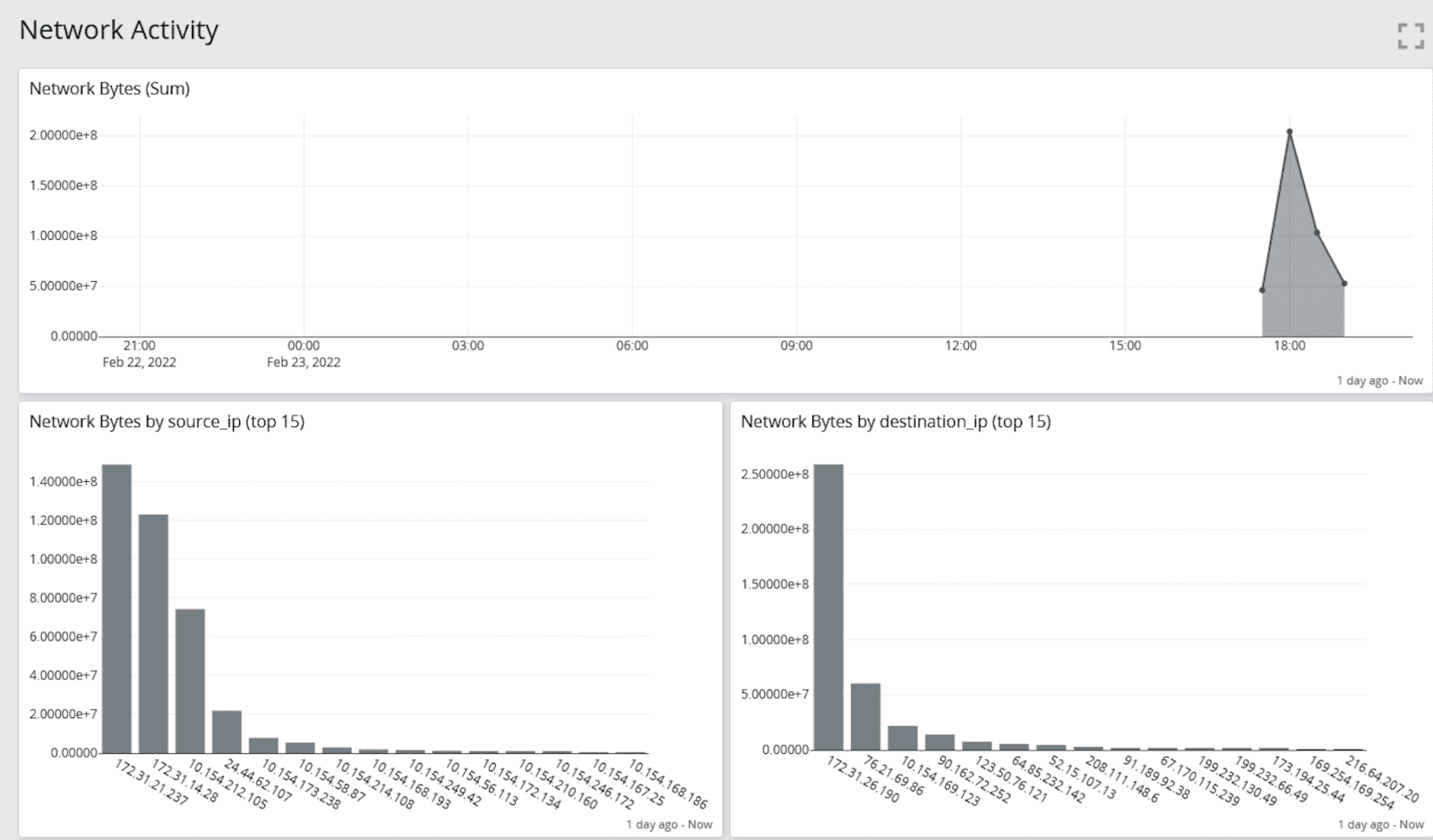
Compliance
Just as your centralized log management solution helps monitor activities and investigate incidents, it also serves for compliance reporting. Senior leadership is advocating for a security intelligence analytics tool to understand the company’s risk posture for compliance mandates.
Utilizing your centralized log management tool for security analytics enables you to achieve this goal. You can generate visualizations offering high-level insights into your security stance. Automation ensures these reports are delivered on schedule, eliminating the need to manually retrieve data repeatedly.
For instance, a dashboard displaying trends over time provides visibility into the organization’s security management effectiveness.
Graylog: Security Intelligence Analytics for Enhanced ROI
With Graylog Security, you gain the essential security analytics without the high costs—both in time and money—associated with SIEM solutions. Leveraging existing skills in centralized log management tools allows IT teams to advance security capabilities effectively.
Graylog offers a dual-purpose solution covering both security and IT operations, maximizing return on investment. Our precise alerts decrease Mean Time to Detect, while rapid search functionalities reduce Mean Time to Investigate and Recover.
Enhancing your security posture needn’t be financially prohibitive. With Graylog as your partner, you acquire essential capabilities without unnecessary complexities.
Source: https://graylog.org/post/security-intelligence-analytics-planning-increases-roi/
About DT Asia
DT Asia began in 2007 with a clear mission to build the market entry for various pioneering IT security solutions from the US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around the Asia Pacific to better understand the markets and deliver localised solutions.










