Cyber resilience frameworks can help your organization achieve a vital goal: ensuring you can prepare for, withstand, recover from and evolve to better adapt to cyberattacks and other threats to your IT systems that can disrupt your business, or even bring it to a screeching halt.
But what cyber resilience frameworks are available? What exactly do they offer? And how do cyber resilience frameworks fit together with venerable resources like the MITRE ATT&CK knowledge base? Read on to get answers to these and other key questions about implementing a cyber resilience framework in your organization.
What is cyber resilience?
Before we dive into cyber resilience frameworks, let’s review what cyber resilience is and how it differs from cybersecurity.
Cybersecurity focuses on preventing cyberattacks and other security incidents from occurring and minimizing the damage they can inflect. It includes measures for keeping adversaries out of the network, such as firewalls and anti-virus tools, and access controls like a least-privilege model and multifactor authentication (MFA), as well as non-technical approaches like security awareness training for users. It also includes strategies for spotting threats in progress and responding to them in time to limit their impact, such as auditing activity across the IT ecosystem, user behavior and entity analytics (UBEA) and change control.
But organizations have come to recognize that while cybersecurity remains a key concern, it is one piece of a larger goal: keeping the business up and running. Accordingly, attention has shifted in recent years to cyber resiliency. Cyber resiliency involves thinking more broadly about adversity, which includes not just adversaries launching malicious attacks on cyber resources, but adverse conditions, stresses or compromises that could affect those resources. Examples include natural disasters, power failures, and unexpectedly high loads.
Working toward cyber resilience also involves taking an assume-breach mindset and understanding that modern attacks often involve stealthy, persistent and sophisticated adversaries. Organizations need to think broadly about what they can do to stay up and running given that there are bad actors who can establish — or have already established — a presence in their IT environment and are therefore positioned to steal critical data and disrupt vital services.
What are cyber resilience frameworks?
Cyber resilience frameworks are guidance — structured best practices and recommended security controls that organizations can adopt to improve their ability to block, withstand and recover from cybersecurity threats. Cyber resilience frameworks do not list hard-and-fast rules to follow or detail a specific set of technologies or products to implement. Rather, they expound upon best practices and provide valuable guidance for improving your cyber resilience. Organizations can and should adapt cyber resilience frameworks to meet their unique goals and requirements.
The foundation: cybersecurity frameworks like the NIST CSF
Cyber resilience frameworks have their roots in cybersecurity frameworks, which are designed to help organizations manage their cybersecurity risk. Perhaps the most well-known is the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). CSF version 1.1 comprises the five core functions illustrated here:
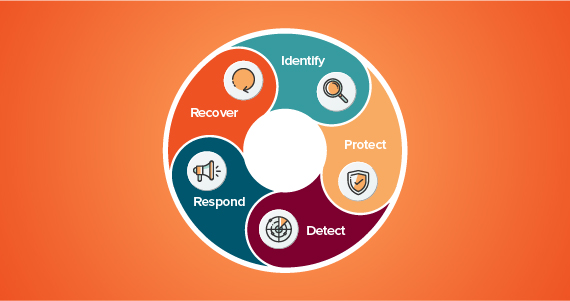
- Identify — Proactively look for indicators of exposure (IOEs), exploitable attack vectors that adversaries could use to enter your IT ecosystem and move laterally, and attack paths that hackers could use to elevate their access to achieve their objectives. Examples include software vulnerabilities, misconfigured devices and nested permissions.
- Protect — Mitigate vulnerabilities according to your risk tolerance. For instance, prevent changes to critical security groups and Group Policy, and remediate the choke points of attack paths.
- Detect — Uncover indicators of compromise (IOCs) with real-time auditing, anomaly detection and alerting.
- Respond — Rapidly gather and analyze information about an incident so you can make informed decisions about the best course of action.
- Recover — Restore systems and data quickly, accurately and effectively.
NIST CSF 2.0 will add a sixth function, Govern. This new function stresses that cybersecurity governance is critical to managing and reducing cybersecurity risk. It is a cross-cutting function that informs and supports the others; for example, governance outcomes inform the prioritization of security controls. Some categories currently covered in other functions will be moved into the Govern function; these could include the “Risk Management Strategy” and “Business Environment” categories of the Identify function.
Expanding from the NIST CSF to a cyber resilience framework
As you can see, the NIST CSF is actually well on the way toward being not just a cybersecurity framework, but a cyber resilience framework. Indeed, many cyber resilience frameworks build upon the five NIST CSF functions, often renaming and expanding them.
In particular, NIST offers publication 800-160 v2, “Developing Cyber-Resilient Systems: A Systems Security Engineering Approach.” It details two important and related concepts for cyber resilience frameworks: cyber resiliency goals and cyber resiliency objectives.
Cyber resiliency goals
Goals are high-level statements of intended outcomes. The four goals described in the NIST guidance are:
- Anticipate — This goal is to maintain a state of informed preparedness for adversity. This involves identifying and mitigating weaknesses, but also contingency planning for threat events to ensure you can investigate and responding to discovery of vulnerabilities or compromises.
- Withstand — This goal is to continue your essential mission or business functions despite adversity. Naturally, this requires identifying your essential mission and business functions, along with all supporting processes, systems, services and infrastructures. It’s important to remember that the criticality of functions and their supporting capabilities can change over time.
- Recover — The third goal is to restore your mission or business functions during and after adversity, possibly using a staged (incremental) process. It’s vital to ensure that recovery does not restore the threat; for example, restoring a system from backup without sufficient precautions might also restore a backdoor that an adversary planted weeks ago.
- Adapt — The final goal is to modify your mission or business functions and their supporting capabilities in response to changes in your IT environment and the threat landscape.
Cyber resiliency objectives
Objectives are more specific statements of intended outcomes. They are expressed in a way that facilitates assessment of “how well” or “how quickly” or “with what degree of confidence or trust” the objective can be achieved. The NIST guidance outlines eight cyber resiliency objectives:
- Prevent or avoid — Preclude the successful execution of an attack or the realization of adverse conditions.
- Prepare — Accept that adversity will occur and maintain a set of realistic responses to address anticipated adversity.
- Continue — Maximize the duration and viability of essential mission or business functions during adversity.
- Constrain — Limit damage from adversity inflicted on high-value assets, such as those that store or process sensitive information or support mission-essential capabilities.
- Reconstitute — Restore as much mission or business functionality as possible after adversity, while ensuring that the restored resources are trustworthy.
- Understand — Maintain useful representations of mission and business dependencies and the status of resources with respect to possible adversity. (Note that this objective supports all the others.)
- Transform — Modify mission or business functions and their supporting processes to better handle adversity. This can include tactical changes to procedures or configurations, as well as broader modifications like restructuring governance responsibilities or operational processes.
- Re-architect — Modify system, mission and supporting architectures to handle adversity more effectively.
MITRE Cyber Resilience Engineering Framework (CREF)
Understanding resiliency goals and objectives is vital for adopting cyber resilience frameworks, but what about actually implementing those goals and objectives in your organization? Enter MITRE.
MITRE is best known for developing and maintaining a comprehensive knowledge base of tactics and techniques used by cyber adversaries. It comprises 14 categories that map roughly to the stages of the cyber kill chain, from reconnaissance and initial access, through privilege escalation and lateral movement, to exfiltration and impact. Organizations worldwide use the MITRE ATT&CK matrix to understand and defend against cyberattacks,
But MITRE also provides the Cyber Resilience Engineering Framework (CREF), which builds upon cyber resilience frameworks like NIST’s by providing not only resiliency goals and objectives but resilience techniques:
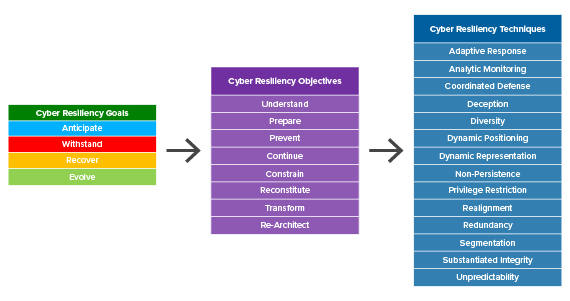
As you can see, the goals and objectives listed by MITRE are quite similar to those identified by NIST. You should feel free to use whichever version better suits your organization’s needs. Here, let’s focus on the cyber resiliency techniques that can help you achieve your cyber resiliency objectives.
Cyber resiliency techniques
MITRE details the following cyber resiliency techniques:
- Adaptive response — Respond dynamically to incidents to maintain operational capabilities and limit damage.
- Analytic monitoring — Continuously collect and analyze data to identify vulnerabilities and indications of possible adversity.
- Coordinated defense — Use a defense-in-depth strategy to protect critical resources.
- Deception — Confuse and mislead adversaries.
- Diversity — Use multiple technologies, data sources, locations and communications paths to reduce the risk of common failures.
- Dynamic positioning — Distribute and dynamically relocate functionality and assets.
- Dynamic representation — Use dynamic representations of components, services, systems, adversities and responses.
- Non-persistence — Limit the time you retain information, services and connectivity to reduce risk of corruption, modification or takeover.
- Privilege restriction — Strictly restrict privileges granted to users and other cyber entities in accordance with least privilege, especially for critical resources.
- Realignment — Adjust the alignment of resources with mission functions to reduce risk.
- Redundancy — Have multiple instances of critical information and resources.
- Segmentation/separation — Separate components, logically or physically, to minimize the spread of damage.
- Substantiated integrity — Implement mechanisms to determine whether critical resources have been corrupted
- Unpredictability — Make frequent and random changes to make your attack surface less predictable.
Keep in mind that the CREF is deliberately incomplete; it does not include resiliency objectives and techniques related non-cyber threats, such as natural disasters and human errors.
Since objectives can support multiple goals, and most techniques support multiple objectives, things can get complicated quickly. For help visualizing the relationships between cyber resiliency goals, objectives and techniques, check out MITRE’s free Cyber Resiliency Engineering Framework Navigator.
Cybersecurity Assessment Framework (CAF)
A vital part of improving your cyber resiliency is having a way to measure it. That way, you can identify the steps to take, prioritize your investments and gauge your progress over time — as well as provide evidence to secure budget for the work.
The Cybersecurity Assessment Framework (CAF) was developed by the National Cyber Security Centre (NCSC) to help improve the security of network and information systems across the UK, especially those that support functions vital to the economy, society, the environment and individuals. However, it can be a valuable tool for any organization interested in assessing its cyber resilience. It provides a systematic and comprehensive approach for assessing the extent to which cyber risks to essential functions are being managed.
The CAF is rooted in 14 principles spread across four objectives. The principles describe outcomes that need to be achieved, rather than providing a checklist of what to do. They are presented in straightforward language:
- Objective A: Managing security risk
- 1 Governance
- 2 Risk management
- 3 Asset management
- 4 Supply chain
- Objective B: Protecting against cyber attack
- 1 Service protection policies and processes
- 2 Identity and access control
- 3 Data security
- 4 System security
- 5 Resilient networks and systems
- 6 Staff awareness and training
- Objective C: Detecting cybersecurity events
- 1 Security monitoring
- 2 Proactive security event discovery
- Objective D: Minimizing the impact of cybersecurity incidents
- 1 Response and recovery planning
- 2 Lessons learned
A CAF assessment evaluates the organization’s cybersecurity posture against these objectives and principles and identifies areas for improvement, such as outdated software, missing patches or insufficient access controls. This information can be used to develop a roadmap for implementing changes to strengthen cyber resilience most effectively. Performing regular CAF assessments also provides organizations with a way to track their progress in improving their cyber resilience.
Center for Internet Security (CIS) security best practices
The Center for Internet Security also offers valuable guidance for improving cyber resilience, which is orthogonal to the cyber resilience frameworks we’ve already explored. The CIS security best practices are a prescriptive and prioritized set of actions that organizations can implement to defend against cyberattacks. They include the CIS Critical Security Controls (CIS Controls) and the CIS Benchmarks.
CIS Critical Security Controls
The CIS Controls detail specific, practical and measurable safeguards to implement, and are regularly updated to reflect changes in technology, best practices and the threat landscape. In Version 8, the controls are organized by activity, rather than by who manages the devices:
- Inventory and control of enterprise assets
- Inventory and control of software assets
- Data protection
- Secure configuration of enterprise assets and software
- Account management
- Access control management
- Continuous vulnerability management
- Audit log management
- Email and web browser protections
- Malware defenses
- Data recovery
- Network infrastructure management
- Network monitoring and defense
- Security awareness and skills training
- Service provider management
- Application software security
- Incident response management
- Penetration testing
For example, Control 11 details the following safeguards for data recovery:
- Establish and maintain a data recovery process.
- Perform automated backups.
- Protect recovery data.
- Establish and maintain an isolated instance of recovery data.
- Test recovery data.
CIS Benchmarks
The CIS Benchmarks detail best practices for secure configuration of a wide variety of systems, including:
- Desktops & web browsers
- Mobile devices
- Network devices
- Servers
- Virtualization platforms
- Microsoft Office applications
ISO/IEC 27001 and 27002
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) provide two related standards for information security, cybersecurity and privacy protection: ISO/IEC 27001 and ISO/IEC 27002.
ISO/IEC 27001 is designed to help organizations build solid foundations for information security. This auditable international standard defines the requirements of an information security management system (ISMS). It specifies requirements for establishing, implementing, maintaining and continually improving an ISMS, and for assessing and remediating information security risks.
Certification to the ISO/IEC 27001 standard demonstrates that an organization follows best-practice information security processes. Organizations that do not choose to get ISO 27001 certified can still use the standard to improve their information security and cyber resilience.
ISO/IEC 27002 complements ISO/IEC 27001 by providing a reference set of generic information security controls. While ISO 27001 explains each control only briefly, ISO 27002 provides significant detail, including implementation guidance. Organizations cannot be certified against ISO 27002 because it is not a management standard.
NIS2 Directive
The Network and Information Security (NIS) Directive, enacted in 2016, was the first piece of EU-wide legislation on cybersecurity, intended to achieve high common level of cybersecurity across EU member states. It requires operators of essential services and digital service providers to take appropriate security measures and to report incidents that significantly impact the availability of their services.
While NIS was a solid first step, there were challenges with implementation, including lack of clarity about the directive’s expectations after transposition into national laws. To address those issues, the EU passed NIS2 in January 2023; member states have until October 18, 2024 to implement the new directive in their respective national laws.
Key changes in NIS2 include the following:
- Personal liability for management teams — Non-compliance with NIS2 can result in enforcement orders and significant fines. Moreover, NIS2 introduces personal liability for company boards, executives and other management bodies.
- Change in organization types — Instead of distinguishing between “operators of essential services” and “digital service providers,” NIS2 distinguishes between “essential entities” and “important entities” based on the sector and size of the operator. Essential entities are subject to stricter enforcement and oversight requirements.
- Expanded scope — Additional organizations are in the scope of the directive. New categories include manufacturers of medical devices, social network providers and food processors.
- New requirements — NIS2 imposes new obligations for incident reporting and risk management, such as supply chain risk management.
- Enhanced collaboration — NIS2 aims to enhance collaboration and knowledge sharing among member states through mechanisms such as peer review.
Cyber resilience frameworks and regulatory compliance
While NIS2 is a directive that applies to many organizations in the EU, most cybersecurity and cyber resilience frameworks are designed to be voluntary and are published by organizations that are not regulatory agencies. Nevertheless, because they are built on established best practices for cybersecurity and cyber resilience, their use is mandated by some regulations.
For example, NIST is not a regulatory agency, but Executive Order 13800, Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure, makes the NIST CIF cyber resilience framework mandatory for U.S. federal government agencies, and other government agencies. Similarly, the NCSC is a national technical authority for cybersecurity, and while it developed the CAF with the expectation that it would be used to support cyber regulation, the NCSC itself has no regulatory responsibilities.
Many other compliance standards draw upon cybersecurity and cyber reliance frameworks. For instance, the Payment Card Industry Data Security Standard (PCI DSS) mandates protecting cardholders’ sensitive information (Requirement 3) and encrypting data transmitted across public networks (Requirement 4). NIST provides industry best practices that can help satisfy these requirements, including methods for implementing encryption and managing encryption keys.
How to get started with cyber resilience frameworks
A critical early step in adopting cyber resilience frameworks is not technical at all — it’s assembling the right team. It’s vital to gain support at the C-suite level. The chief security officer (CSO) or chief information security officer (CISO) are essential for gaining a clear picture of how the framework fits into their missions. But it’s best to have buy-in from as many others as possible, such as the chief executive, financial, privacy and risk officers. While acquiring budget is one crucial reason for involving them, it’s not the only one: Embracing cyber resilience requires changes in both policy and culture, which needs to be driven and supported from the C level down.
Then there’s the matter of choosing a framework. As we have seen, cyber resilience frameworks are built from the same foundations: well-known best practices. Accordingly, it matters less which framework you pick than that you simply get started. Core areas to tackle include:
- Understand your organization’s mission and business functionsand their supporting processes and tools. Determine what’s essential to keeping your organization moving along, even if it’s not running at full speed. That’s where you want to focus your attention first. In any Microsoft-based environment, Active Directory is at the top of the list, so be sure to include cybersecurity risk management for Active Directory.
- Adopt an assume-breach mindset.Actually, adopt an assume-adversity As we have seen, adversity comes not only in the form of external cyberattacks, but insider threats, mistakes, equipment failures, natural disasters and more. Begin asking how you can both mitigate the risk of adversity occurring and how you can respond most effectively when it does, so you can keep your operations from grinding to a halt.
- Remember that cyber resilience is a journey, not a destination. Set expectations for everyone — the IT team, business users, the C-suite — that no cyber resilience strategy is perfect, nor could one remain perfect in the face of constant change in technology, processes and the threat landscape. Cyber resilience frameworks are designed to provide high-level guidance and are revised regularly for just that reason.
Conclusion
Cyber resilience frameworks provide organizations with invaluable best-practice guidance that helps them prepare for, withstand, recover from and adapt to adversity, from cyberattacks to natural disasters.
There’s no need to be intimidated by the wide range of cyber resilience frameworks and related resources that are available. The NIST cyber resilience framework is a great place to start; it elucidates the core goals and objectives that are the backbone of a strong strategy. When you’re ready to begin implementation, MITRE details the cyber resilience techniques you need to know about, and NIS2 offers pragmatic and actionable guidance that is valuable even for organizations that are not in its scope.
Hopefully, this article helps get you started on your path to better cyber resilience.
Source: https://blog.quest.com/the-most-common-cyber-resilience-frameworks-to-know/
About DT Asia
DT Asia began in 2007 with a clear mission to build the market entry for various pioneering IT security solutions from the US, Europe and Israel.
Today, DT Asia is a regional, value-added distributor of cybersecurity solutions providing cutting-edge technologies to key government organisations and top private sector clients including global banks and Fortune 500 companies. We have offices and partners around the Asia Pacific to better understand the markets and deliver localised solutions.











