For IT and security teams, the pressure to manage vast amounts of log and event data has never been greater. As digital environments expand and threats evolve, the need for reliable visibility and actionable insights is more urgent than ever. Yet, many organizations are still relying on outdated approaches that strain resources, compromise data quality, and inflate costs.
Beyond Basic Monitoring: Why Enriched NetFlow is Your Key to True Network Observability
In today’s fast-evolving digital landscape, simply monitoring your network is no longer enough. Traditional tools may confirm whether devices are up or down, but they fall short in delivering the actionable insights needed to understand network behavior, resolve performance issues, or spot advanced threats before they strike.
KnowBe4 Deploys Additional Agentic Capabilities to Bolster Customers’ AI Defenses
KnowBe4, the global leader in cybersecurity and human risk management (HRM), is celebrating the success of its customers who have achieved groundbreaking results in strengthening their security posture. Leveraging the HRM+ platform and advanced AI-powered solutions—including AIDA (Artificial Intelligence Defense Agents)—organizations like First Community Credit Union have reduced their Phish-prone Percentage (PPP) to an impressive near-perfect one percent.
5 Reasons for Choosing vSEC:CMS for Passkey Deployment
Unlock the Future of Passkey Deployment with vSEC:CMS
#SecureCommunications: Why Data Sovereignty Is No Longer Optional
For years, organizations have embraced the convenience, cost savings, and speed of global cloud platforms. But in today’s geopolitical climate—where digital infrastructure is inseparable from national security—outsourcing critical communications to foreign-controlled services carries significant risks.
Defending your organization before, during and after a cyberattack
If you’ve ever worked in IT during a cyberattack, you know the sinking feeling.
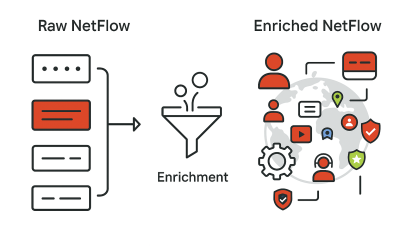
The Value of Data Enrichment in Cybersecurity Data
Imagine standing in the cereal aisle, comparing two boxes. One is your favorite sugary delight, and the other is a fiber-packed, vitamin-enriched option. While your taste buds may prefer the sugary pick, your body benefits far more from the extra nutrients in the healthier option.
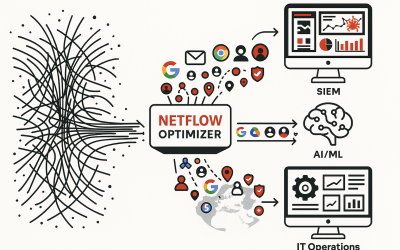
Automating Threat Hunting: How Optimized NetFlow Fuels AI-Driven Security Operations
Today’s cybersecurity landscape is a fast-moving battleground. Security operations teams are overwhelmed by an endless stream of advanced threats buried deep within vast amounts of network data. Manual threat hunting—digging through logs and alerts—is no longer practical. The pace and complexity of modern attacks demand automation. Enter NetFlow, AI, and the critical process of optimization.
Weighing the Risks: External Hard Drive vs. Cloud-Based Storage
Choosing the right place to store your important data isn’t as straightforward as it used to be. Between convenient cloud services and the physical control of external hard drives, it can be hard to decide which is best—especially when factoring in security, accessibility, and long-term reliability.
Parsing firewall logs with FilterX
Your SIEM is only as good as the data it ingests. But when firewall logs from major vendors like FortiGate, Palo Alto, and SonicWall arrive incomplete, inconsistent, or malformed, most syslog pipelines struggle to keep up.
Protect Personal Info With RFID Blocking Cards
In today’s hyper-connected world, protecting personal information is more important than ever. As technology evolves, so do the methods cybercriminals use to access and exploit sensitive data. From financial transactions to identity documents, our growing dependence on digital systems makes us increasingly vulnerable to information theft. One emerging threat in this space is RFID skimming—a technique used to silently steal data from RFID-enabled cards like credit cards, passports, and access cards, often without the victim ever realizing it.
The Importance of Triage in Incident Response
If you’re a gamer of a certain generation, you probably remember the arcade classic Asteroids. You piloted a tiny triangular ship, dodging and shooting incoming space rocks that started slow but gradually sped up. Success required rapid decision-making—figuring out which rocks posed a real threat and which you could afford to ignore.
About Us
From hardware appliances to software solutions and training, DT Asia understands cybersecurity challenges and can deliver solutions that help detect & identify, protect & secure, authenticate & authorise, and degauss & destroy.
Contact Us
Address
#02-72 WCEGA Tower,
Singapore 658065