May 24, 2023 | Uncategorized
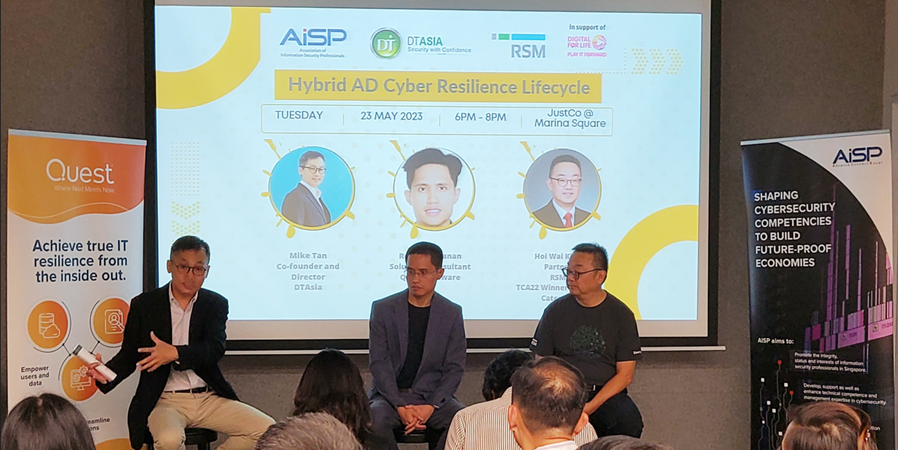
We had a great collaboration with — AiSP, RSM and Quest – on “Hybrid AD Cyber Resilience Lifecycle” and our combined efforts led to a successful panel engagement with the attendees, on 23 May.

May 16, 2023 | Events, Events, Events
Embracing the “new normal”, the Ministry of Information and Communications together with the Authority of Information Security (MIC) and IEC Group will be hosting the fifth annual Vietnam Security Summit in Ho Chi Minh City within a safe and inspiring environment on...

May 10, 2023 | Uncategorized
Our recent company bonding trip @ ClubMed on 4-6 May was a huge success! It was great to have our teams across the region, come together to build a stronger bonding relationship outside of work! We had great fun – connecting together and creating memories...