Các vụ rò rỉ dữ liệu đang ngày càng trở nên phổ biến, với các nghiên cứu gần đây cho thấy trong năm 2024, hơn 16,8 tỷ bản ghi đã bị lộ do các sự cố dữ liệu. Con số này tương đương với khoảng 533 bản ghi bị xâm phạm mỗi giây suốt cả năm. Thống kê đáng báo động này nhấn mạnh nhu cầu cấp thiết về giải pháp mã hóa dữ liệu mạnh mẽ và các phương thức quản lý hiệu quả. Ổ đĩa mã hóa là những thiết bị lưu trữ được trang bị các thuật toán mã hóa tiên tiến, đóng vai trò quan trọng trong việc bảo vệ thông tin nhạy cảm khỏi truy cập trái phép. Công nghệ quản lý từ xa cho phép người dùng quản trị các ổ đĩa mã hóa này một cách an toàn từ mọi vị trí, mang lại mức độ tiện lợi vượt trội.
Các chuyên gia tại SecureData giải thích cách mà quản lý từ xa mang lại sự tiện lợi mà không phải hy sinh tính bảo mật của các ổ đĩa mã hóa.
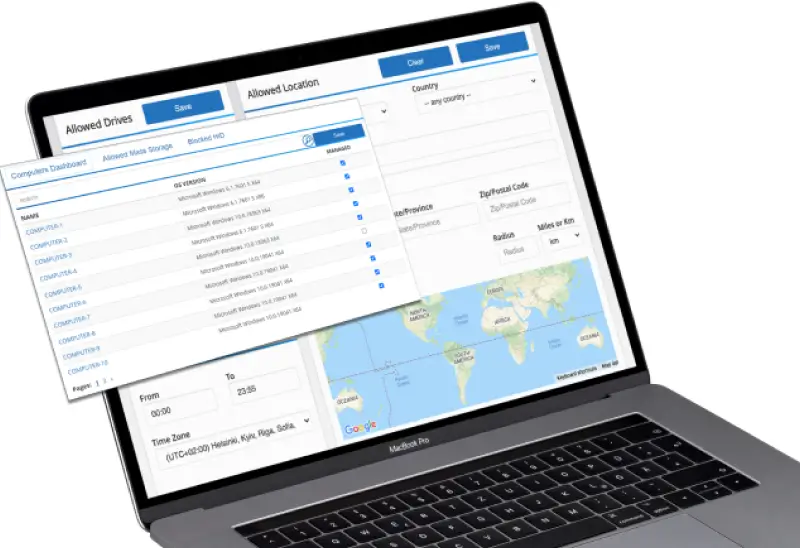
Quản lý từ xa là gì?
Quản lý từ xa đề cập đến khả năng truy cập và điều khiển các ổ đĩa mã hóa một cách an toàn từ bất kỳ vị trí địa lý nào thông qua kết nối mạng. Về cơ bản, công nghệ quản lý từ xa bao gồm các công cụ phần mềm chuyên dụng giúp xác thực các quản trị viên hoặc người dùng được ủy quyền, cho phép họ cấu hình, giám sát và khắc phục sự cố ổ đĩa ngoài mã hóa và USB flash drive mà không cần tiếp xúc vật lý. Việc xác thực thường sử dụng các phương pháp xác minh danh tính mạnh mẽ như xác thực đa yếu tố (MFA) và các giao thức truyền thông an toàn để đảm bảo quyền riêng tư và tính toàn vẹn của dữ liệu.
Các tiêu chuẩn mã hóa như AES-256 (Advanced Encryption Standard với độ dài khóa 256 bit) cung cấp một lớp bảo mật nền tảng mạnh mẽ, giúp đảm bảo dữ liệu nhạy cảm không thể bị truy cập bởi những người không được phép. Khi quản lý các ổ đĩa mã hóa từ xa, cơ chế mã hóa sẽ bảo vệ dữ liệu được truyền qua các mạng có thể không an toàn, qua đó giảm thiểu đáng kể nguy cơ bị chặn hoặc truy cập trái phép.
Sự tiện lợi của quản lý từ xa đối với ổ đĩa mã hóa
Việc tích hợp công nghệ quản lý từ xa vào các giải pháp ổ đĩa mã hóa giúp nâng cao đáng kể sự tiện lợi trong vận hành cho cả cá nhân lẫn tổ chức. Một trong những lợi ích chính là khả năng quản lý đồng thời nhiều ổ đĩa mã hóa thông qua một giao diện tập trung, từ đó tối ưu các tác vụ quản trị và giảm bớt sự phức tạp vốn có trong bảo mật dữ liệu.
Chẳng hạn, doanh nghiệp có thể thực hiện cập nhật firmware, điều chỉnh cài đặt mã hóa, chạy chẩn đoán, hoặc thậm chí khởi tạo quy trình xóa dữ liệu an toàn — tất cả từ xa mà không cần can thiệp trực tiếp vào thiết bị. Khả năng này giúp giảm thiểu đáng kể thời gian gián đoạn, vì các sự cố có thể được xử lý nhanh chóng thay vì phải chờ đợi quy trình thủ công tại chỗ.
Bên cạnh đó, quản lý từ xa đối với các ổ đĩa mã hóa còn mang lại sự linh hoạt quan trọng, đặc biệt đối với các đội ngũ làm việc phân tán hoặc nhân viên làm việc từ xa. Quản trị viên có thể truy cập an toàn vào các hệ thống quan trọng bất cứ lúc nào và từ bất kỳ vị trí nào, giúp nâng cao năng suất và hiệu quả trong toàn bộ quy trình vận hành của tổ chức.
Quản lý từ xa dành cho người dùng cá nhân
Mặc dù công nghệ quản lý từ xa thường được biết đến nhiều trong môi trường doanh nghiệp, người dùng cá nhân cũng có thể hưởng lợi đáng kể từ các tính năng mà nó mang lại. Những người làm việc tự do, chuyên gia làm việc từ xa hoặc những cá nhân cần quản lý thông tin cá nhân nhạy cảm đều có thể sử dụng ổ đĩa mã hóa có hỗ trợ quản lý từ xa để duy trì mức độ bảo mật dữ liệu cao mà vẫn đảm bảo sự tiện lợi.
Ví dụ, những người thường xuyên di chuyển hoặc làm việc từ nhiều địa điểm khác nhau có thể truy cập và quản lý ổ đĩa mã hóa của họ một cách an toàn từ bất kỳ đâu, mà không phải đối mặt với rủi ro khi mang theo dữ liệu nhạy cảm. Tính năng xóa dữ liệu từ xa (remote wipe) còn giúp bảo vệ người dùng tốt hơn bằng cách cho phép xóa dữ liệu nhanh chóng nếu thiết bị bị mất hoặc bị đánh cắp.
Cân bằng giữa tiện lợi và bảo mật
Mặc dù quản lý từ xa đối với ổ đĩa mã hóa mang lại sự tiện lợi đáng kể, bản thân nó cũng có thể tạo ra một số điểm dễ tổn thương về bảo mật. Để giải quyết những rủi ro này, các hệ thống quản lý từ xa hiện đại ứng dụng những biện pháp bảo mật tiên tiến được thiết kế đặc biệt nhằm giảm thiểu các lỗ hổng:
Xác thực đa yếu tố (MFA)
- Yêu cầu nhiều hình thức xác minh trước khi cấp quyền truy cập.
- Đảm bảo chỉ những cá nhân được ủy quyền mới có thể quản lý ổ đĩa mã hóa.
- Giảm thiểu mạnh mẽ nguy cơ bị đánh cắp thông tin đăng nhập hoặc truy cập trái phép
Zero-Trust Architecture
- Áp dụng cơ chế xác minh nghiêm ngặt cho mọi yêu cầu truy cập, không phân biệt nguồn gốc mạng.
- Loại bỏ sự tin cậy ngầm, giúp bảo vệ hệ thống ngay cả trước các mối đe dọa từ bên trong.
- Tăng cường mức độ an toàn bảo mật thông qua việc xác thực và đánh giá liên tục người dùng và thiết bị.
Các kênh truyền thông an toàn (Secure Communication Channels)
- Sử dụng VPN mã hóa đầu-cuối và các giao thức SSL/TLS.
- Đảm bảo tính bảo mật và toàn vẹn của dữ liệu được truyền trong quá trình quản trị từ xa.
- Bảo vệ khỏi nguy cơ nghe lén, tấn công trung gian (man-in-the-middle) và giả mạo dữ liệu.
Kiểm soát truy cập chi tiết (Granular Access Controls)
- Cho phép thiết lập quyền truy cập người dùng một cách chính xác dựa trên vai trò và trách nhiệm.
- Giới hạn quyền truy cập vào các chức năng hoặc dữ liệu nhạy cảm của ổ đĩa chỉ cho những nhân sự thực sự cần thiết.
- Giảm thiểu nguy cơ đe dọa nội bộ và các sự cố rò rỉ dữ liệu do vô tình.
Khả năng giới hạn theo vị trí và thời gian (Geo-Fencing and Time-Fencing Capabilities)
- Hạn chế quyền truy cập vào ổ đĩa được mã hóa theo khu vực địa lý hoặc khung thời gian xác định.
- Ngăn chặn việc sử dụng trái phép từ các vị trí không quen thuộc hoặc vào những thời điểm không được phép.
- Bổ sung thêm một lớp bảo mật, tăng cường khả năng kiểm soát thời điểm và địa điểm truy cập ổ đĩa.
Nhật ký kiểm toán toàn diện (Comprehensive Audit Logs)
- Ghi nhận chi tiết toàn bộ nhật ký hoạt động của các tác vụ quản lý từ xa.
- Hỗ trợ minh bạch và tuân thủ các quy định, tiêu chuẩn của ngành.
- Cho phép nhanh chóng xác định và điều tra các sự cố an ninh hoặc hành vi bất thường.
Góc nhìn kỹ thuật và ứng
Dưới đây là một số tính năng và ứng dụng tốt nhất cho quản lý từ xa (Remote Management):
1. Quản lý khóa tập trung
- Tạo và phân phối khóa an toàn
- Lưu trữ khóa được bảo vệ
- Thực hiện xoay vòng khóa định kỳ
- Hủy khóa an toàn sau khi không còn sử dụng
2. Khả năng xóa dữ liệu từ xa
- Cho phép xóa dữ liệu an toàn và ngay lập tức đối với các ổ đĩa bị mất, bị đánh cắp hoặc bị xâm nhập.
- Ngăn chặn truy cập trái phép và giảm thiểu rủi ro rò rỉ dữ liệu.
3. Nhật ký kiểm toán chi tiết
- Duy trì hệ thống nhật ký toàn diện, ghi lại mọi hoạt động quản lý từ xa.
- Tăng cường tính minh bạch, hỗ trợ phân tích pháp y và đảm bảo tuân thủ các quy định.
4. Cập nhật firmware từ xa an toàn
- Thực hiện cập nhật firmware an toàn từ xa một cách thường xuyên để vá các lỗ hổng bảo mật.
- Đảm bảo các ổ đĩa được mã hóa luôn vững chắc trước các mối đe dọa và hình thức khai thác mới.
5. Đánh giá bảo mật định kỳ
- Tiến hành đánh giá định kỳ hệ thống và cấu hình quản lý từ xa, bao gồm:
- Quyền truy cập và vai trò người dùng
- Chính sách xác thực và phân quyền
- Nhật ký bảo mật và báo cáo sự cố
6. Đào tạo quản trị viên liên tục
- Cung cấp đào tạo thường xuyên cho đội ngũ quản trị về các mối đe dọa mới, công cụ và ứng dụng bảo mật tốt nhất.
- Xây dựng văn hóa bảo mật chủ động, có hiểu biết nhằm tăng cường năng lực phòng thủ của tổ chức.
Cam kết của SecureData về sự tiện lợi và bảo mật
Quản lý từ xa các ổ đĩa được mã hóa giúp thu hẹp hiệu quả khoảng cách giữa tính tiện lợi trong vận hành và yêu cầu bảo mật dữ liệu nghiêm ngặt. Thông qua việc áp dụng các thực hành kỹ thuật tiên tiến và nhấn mạnh các giao thức mã hóa mạnh mẽ, doanh nghiệp cũng như người dùng cá nhân có thể tự tin bảo vệ những thông tin nhạy cảm nhất mà không làm ảnh hưởng đến tính dễ sử dụng hay năng suất làm việc.
SecureData cung cấp các giải pháp quản lý từ xa cho ổ đĩa mã hóa hàng đầu trong ngành, cân bằng tối ưu giữa sự tiện lợi và các tiêu chuẩn bảo mật vượt trội. Hãy liên hệ với chúng tôi để trao đổi trực tiếp với chuyên gia và thảo luận về nhu cầu của bạn.
Về DT Asia
DT Asia được thành lập năm 2007 với sứ mệnh đưa các giải pháp bảo mật CNTT tiên phong khác nhau từ Hoa Kỳ, Châu Âu và Israel gia nhập thị trường.
Hiện tại, DT Asia đã là một nhà phân phối giá trị gia tăng trong khu vực đối với các giải pháp an ninh mạng, cung cấp công nghệ tiên tiến cho các tổ chức chính phủ trọng yếu cũng như các khách hàng tư nhân lớn bao gồm các ngân hàng toàn cầu và các công ty trong danh sách Fortune 500. Với các văn phòng và đối tác rộng khắp trong khu vực Châu Á Thái Bình Dương, chúng tôi hiểu rõ hơn về thị trường và từ đó mang đến những giải pháp bản địa hóa phù hợp với từng quốc gia, từng tổ chức.
Cách chúng tôi có thể giúp
Nếu bạn muốn biết thêm về việc Lợi ích của SecureData Remote Management, chúng tôi sẵn sàng giúp đỡ! DT Asia là nhà phân phối của Securaze, đặc biệt tại Việt Nam và châu Á, các kỹ thuật viên của chúng tôi có kinh nghiệm sâu rộng về sản phẩm và các công nghệ liên quan mà bạn luôn có thể tin tưởng. Chúng tôi cung cấp các giải pháp trọn gói cho sản phẩm này, bao gồm tư vấn, triển khai và dịch vụ bảo trì.
Để biết thêm thông tin chi tiết và được hỗ trợ, vui lòng truy cập: https://dtasiagroup.com/secure-data/